Curious about Actual PECB Certified ISO/IEC 27005 Risk Manager Exam Questions?
Here are sample PECB Certified ISO/IEC 27005 Risk Manager (ISO-IEC-27005-Risk-Manager) Exam questions from real exam. You can get more PECB ISO/IEC 27005 Risk Manager (ISO-IEC-27005-Risk-Manager) Exam premium practice questions at TestInsights.
Scenario 2: Travivve is a travel agency that operates in more than 100 countries. Headquartered in San Francisco, the US, the agency is known for its personalized vacation packages and travel services. Travivve aims to deliver reliable services that meet its clients' needs. Considering the impact of information security in its reputation, Travivve decided to implement an information security management system (ISMS) based on ISO/IEC 27001. In addition, they decided to establish and implement an information security risk management program. Based on the priority of specific departments in Travivve, the top management decided to initially apply the risk management process only in the Sales Management Department. The process would be applicable for other departments only when introducing new technology.
Travivve's top management wanted to make sure that the risk management program is established based on the industry best practices. Therefore, they created a team of three members that would be responsible for establishing and implementing it. One of the team members was Travivve's risk manager who was responsible for supervising the team and planning all risk management activities. In addition, the risk manager was responsible for monitoring the program and reporting the monitoring results to the top management.
Initially, the team decided to analyze the internal and external context of Travivve. As part of the process of understanding the organization and its context, the team identified key processes and activities. Then, the team identified the interested parties and their basic requirements and determined the status of compliance with these requirements. In addition, the team identified all the reference documents that applied to the defined scope of the risk management process, which mainly included the Annex A of ISO/IEC 27001 and the internal security rules established by Travivve. Lastly, the team analyzed both reference documents and justified a few noncompliances with those requirements.
The risk manager selected the information security risk management method which was aligned with other approaches used by the company to manage other risks. The team also communicated the risk management process to all interested parties through previously established communication mechanisms. In addition, they made sure to inform all interested parties about their roles and responsibilities regarding risk management. Travivve also decided to involve interested parties in its risk management activities since, according to the top management, this process required their active participation.
Lastly, Travivve's risk management team decided to conduct the initial information security risk assessment process. As such, the team established the criteria for performing the information security risk assessment which included the consequence criteria and likelihood criteria.
Based on scenario 2, the team decided to involve interested parties in risk management activities. Is this a good practice?
Correct : B
According to ISO/IEC 27005, involving relevant interested parties in the risk management process is considered a best practice. This approach ensures that all perspectives are considered, and relevant knowledge is leveraged, which helps in comprehensively identifying, analyzing, and managing risks. Interested parties, such as stakeholders, can provide valuable insights and information regarding the organization's assets, processes, threats, and vulnerabilities, contributing to a more accurate and effective risk assessment. Therefore, option B is correct because it supports the principle that involving relevant parties leads to a more successful risk assessment process. Options A and C are incorrect because excluding either external interested parties or restricting involvement only to the risk management team would limit the effectiveness of the risk management process.
Start a Discussions
What type of process is risk management?
Correct : A
Risk management is an ongoing process that involves continuous monitoring, assessment, and mitigation of risks to ensure that they remain within acceptable levels. According to ISO/IEC 27005, risk management is not a one-time activity but a continuous cycle that includes risk identification, risk analysis, risk evaluation, and risk treatment. The process must be regularly reviewed and updated to respond to changes in the organization's environment, technological landscape, or operational conditions. Option A correctly identifies risk management as an ongoing process. Options B and C are incorrect; risk management is not limited to being conducted simultaneously with internal audits (B), nor is it required to be conducted annually (C).
Start a Discussions
An organization decided to use nonnumerical categories, i.e., low, medium, and high for describing consequence and probability. Which risk analysis methodology is the organization using?
Correct : C
A qualitative risk analysis method uses nonnumerical categories such as low, medium, and high to describe the consequences and probability of risks. This method involves subjective judgment based on expertise, experience, and intuition rather than mathematical calculations. Qualitative methods are often used when it is challenging to obtain accurate numerical data, and they provide a general understanding of risks to prioritize them for further action. Option C is correct because the use of nonnumerical categories aligns with the qualitative risk analysis methodology. Option A (Quantitative) is incorrect as it involves numerical values and statistical methods, while Option B (Semi-quantitative) is a mix of qualitative and quantitative methods, usually involving ranges of numerical values.
Start a Discussions
What should an organization do after it has established the risk communication plan?
Correct : C
Once an organization has established a risk communication plan, it should implement it by establishing both internal and external communication channels to ensure all stakeholders are informed and involved in the risk management process. This step is crucial for maintaining transparency, ensuring clarity, and fostering a collaborative environment where risks are managed effectively. Therefore, option C is the correct answer.
ISO/IEC 27005:2018, Clause 7, 'Communication and Consultation,' which outlines the importance of establishing both internal and external communication mechanisms to ensure effective risk management.
Start a Discussions
Scenario 8: Biotide is a pharmaceutical company that produces medication for treating different kinds of diseases. The company was founded in 1997, and since then it has contributed in solving some of the most challenging healthcare issues.
As a pharmaceutical company, Biotide operates in an environment associated with complex risks. As such, the company focuses on risk management strategies that ensure the effective management of risks to develop high-quality medication. With the large amount of sensitive information generated from the company, managing information security risks is certainly an important part of the overall risk management process. Biotide utilizes a publicly available methodology for conducting risk assessment related to information assets. This methodology helps Biotide to perform risk assessment by taking into account its objectives and mission. Following this method, the risk management process is organized into four activity areas, each of them involving a set of activities, as provided below.
1. Activity area 1: The organization determines the criteria against which the effects of a risk occurring can be evaluated. In addition, the impacts of risks are also defined.
2. Activity area 2: The purpose of the second activity area is to create information asset profiles. The organization identifies critical information assets, their owners, as well as the security requirements for those assets. After determining the security requirements, the organization prioritizes them. In addition, the organization identifies the systems that store, transmit, or process information.
3. Activity area 3: The organization identifies the areas of concern which initiates the risk identification process. In addition, the organization analyzes and determines the probability of the occurrence of possible threat scenarios.
4. Activity area 4: The organization identifies and evaluates the risks. In addition, the criteria specified in activity area 1 is reviewed and the consequences of the areas of concerns are evaluated. Lastly, the level of identified risks is determined.
The table below provides an example of how Biotide assesses the risks related to its information assets following this methodology:
Based on the scenario above, answer the following question:
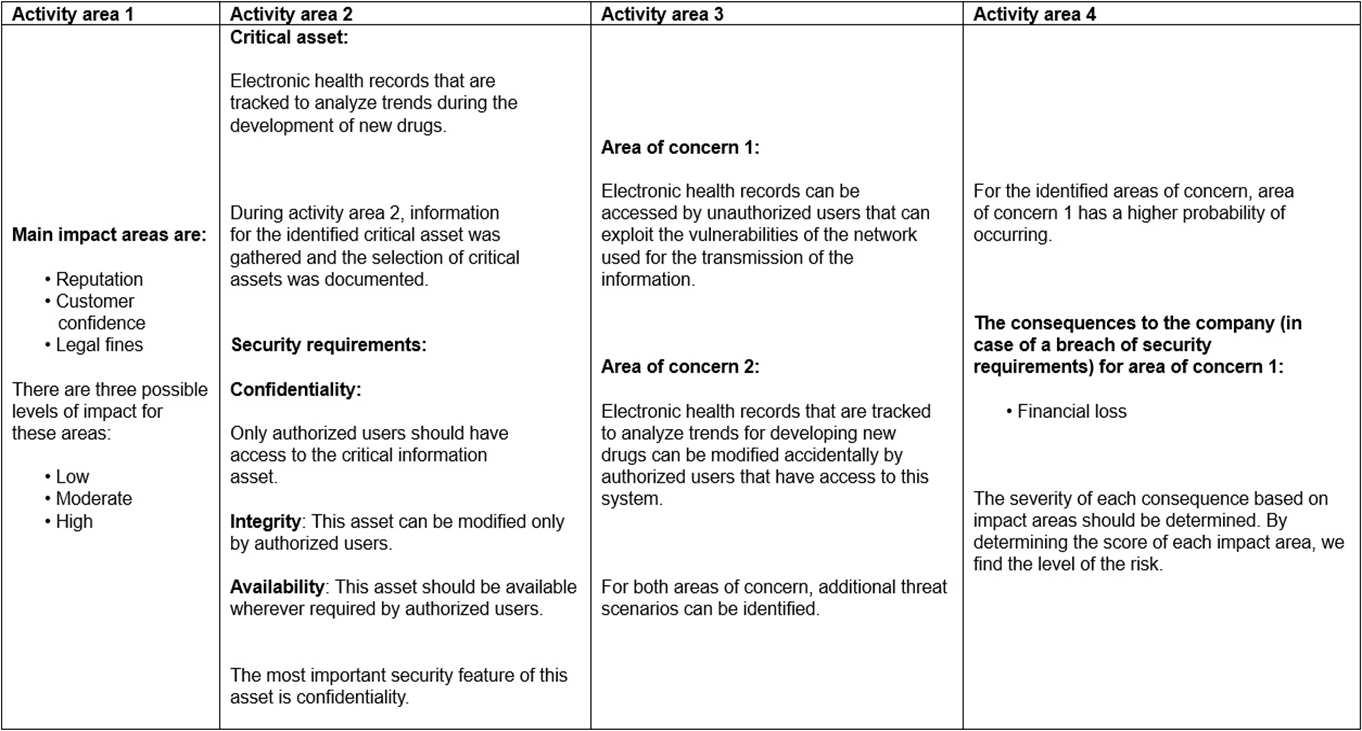
Which risk assessment methodology does Biotide use?
Correct : A
Biotide uses the OCTAVE Allegro methodology for risk assessment. This is determined based on the description of the activities mentioned in the scenario. OCTAVE Allegro is a streamlined approach specifically designed to help organizations perform risk assessments that are efficient and effective, particularly when handling information assets. The methodology focuses on a thorough examination of information assets, the threats they face, and the impact of those threats.
Activity Area 1: OCTAVE Allegro defines the criteria for evaluating the impact of risks, which is consistent with determining the risk effects' evaluation criteria in the scenario.
Activity Area 2: In OCTAVE Allegro, a critical step is creating profiles for information assets, identifying their owners, and determining security requirements. This aligns with the activity in which Biotide identifies critical assets, their owners, and their security needs.
Activity Area 3: Identifying areas of concern that initiate risk identification and analyzing threat scenarios is central to OCTAVE Allegro. This is reflected in the activity of identifying areas of concern and determining the likelihood of threats.
Activity Area 4: Evaluating the risks, reviewing criteria, and determining risk levels corresponds to the latter stages of OCTAVE Allegro, where risks are prioritized based on the likelihood and impact, and risk management strategies are formulated accordingly.
The steps outlined align with the OCTAVE Allegro approach, which focuses on understanding and addressing information security risks comprehensively and in line with organizational objectives. Hence, option A, OCTAVE Allegro, is the correct answer.
ISO/IEC 27005:2018 emphasizes the importance of using structured methodologies for information security risk management, like OCTAVE Allegro, to ensure that risks are consistently identified, assessed, and managed in accordance with organizational risk tolerance and objectives.
Start a Discussions
Total 60 questions