Curious about Actual Netskope Cloud Security Certification Program (NSK200) Exam Questions?
Here are sample Netskope Certified Cloud Security Integrator (NSK200) Exam questions from real exam. You can get more Netskope Cloud Security Certification Program (NSK200) Exam premium practice questions at TestInsights.
A customer wants to use Netskope to prevent PCI data from leaving the corporate sanctioned OneDrive instance. In this scenario. which two solutions would assist in preventing data exfiltration? (Choose two.)
Start a Discussions
Netskope support advised you to enable DTLS for belter performance. You added firewall rules to allow UDP port 443 traffic. These settings are part of which configuration element when enabled in the Netskope tenant?
Start a Discussions
You are comparing the behavior of Netskope's Real-time Protection policies to API Data Protection policies. In this Instance, which statement is correct?
Start a Discussions
Review the exhibit.
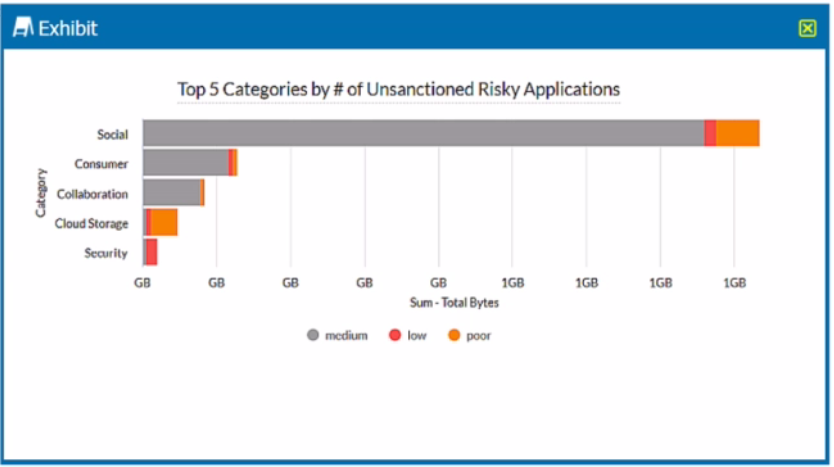
A security analyst needs to create a report to view the top five categories of unsanctioned applications accessed in the last 90 days. Referring to the exhibit, what are two data collections in Advanced Analytics that would be used to create this report? (Choose two.)
Start a Discussions
Your customer has some managed Windows-based endpoints where they cannot add any clients or agents. For their users to have secure access to their SaaS application, you suggest that the customer use Netskope's Explicit Proxy.
Which two configurations are supported for this use case? (Choose two.)
Start a Discussions
Total 93 questions