Curious about Actual Linux Foundation Kubernetes Security Specialist (CKS) Exam Questions?
Here are sample Linux Foundation Certified Kubernetes Security Specialist (CKS) Exam questions from real exam. You can get more Linux Foundation Kubernetes Security Specialist (CKS) Exam premium practice questions at TestInsights.
Using the runtime detection tool Falco, Analyse the container behavior for at least 20 seconds, using filters that detect newly spawning and executing processes in a single container of Nginx.
store the incident file art /opt/falco-incident.txt, containing the detected incidents. one per line, in the format
[timestamp],[uid],[processName]
Correct : A
Start a Discussions
Cluster:qa-cluster Master node:masterWorker node:worker1 You can switch the cluster/configuration context using the following command: [desk@cli] $kubectl config use-context qa-cluster Task: Create a NetworkPolicy namedrestricted-policyto restrict access to Podproductrunning in namespacedev. Only allow the following Pods to connect to Pod products-service: 1. Pods in the namespaceqa 2. Pods with labelenvironment: stage, in any namespace
Correct : A
Start a Discussions
Context
A container image scanner is set up on the cluster, but it's not yet fully integrated into the cluster s configuration. When complete, the container image scanner shall scan for and reject the use of vulnerable images.
Task
Given an incomplete configuration in directory /etc/kubernetes/epconfig and a functional container image scanner with HTTPS endpoint https://wakanda.local:8081 /image_policy :
1. Enable the necessary plugins to create an image policy
2. Validate the control configuration and change it to an implicit deny
3. Edit the configuration to point to the provided HTTPS endpoint correctly
Finally, test if the configuration is working by trying to deploy the vulnerable resource /root/KSSC00202/vulnerable-resource.yml.

Correct : A
Start a Discussions
You must complete this task on the following cluster/nodes: Cluster:immutable-cluster Master node:master1 Worker node:worker1
You can switch the cluster/configuration context using the following command: [desk@cli] $kubectl config use-context immutable-cluster
Context: It is best practice to design containers to be stateless and immutable. Task: Inspect Pods running in namespaceprodand delete any Pod that is either not stateless or not immutable. Use the following strict interpretation of stateless and immutable: 1. Pods being able to store data inside containers must be treated as not stateless. Note:You don't have to worry whether data is actually stored inside containers or not already. 2. Pods being configured to beprivilegedin any way must be treated as potentially not stateless or not immutable.
Correct : A
Start a Discussions
Context
A CIS Benchmark tool was run against the kubeadm-created cluster and found multiple issues that must be addressed immediately.
Task
Fix all issues via configuration and restart the affected components to ensure the new settings take effect.
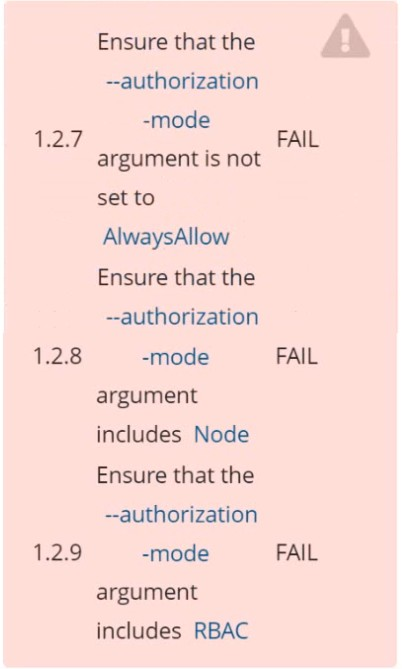
Fix all of the following violations that were found against the API server:
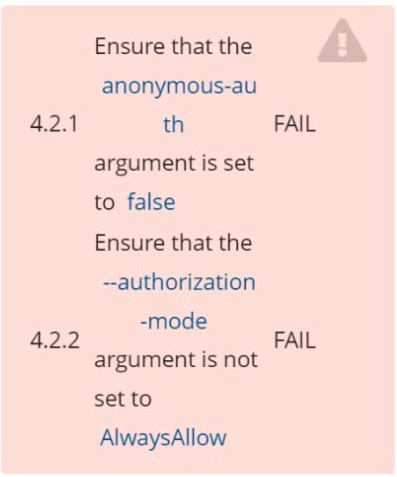
Fix all of the following violations that were found against the Kubelet:

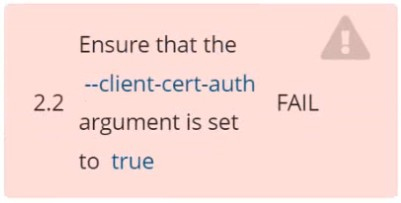
Fix all of the following violations that were found against etcd:
Correct : A
Start a Discussions
Total 48 questions