Curious about Actual Juniper Junos Security Certification (JN0-335) Exam Questions?
Here are sample Juniper Security, Specialist (JN0-335) Exam questions from real exam. You can get more Juniper Junos Security Certification (JN0-335) Exam premium practice questions at TestInsights.
How does Juniper ATP Cloud protect a network from zero-day threats?
Correct : C
Juniper ATP Cloud is a cloud-based service that provides advanced threat prevention and detection for your network. It integrates with SRX Series firewalls and MX Series routers to analyze files and network traffic for signs of malicious activity. Juniper ATP Cloud protects a network from zero-day threats by using dynamic analysis, which is a method of executing files in a sandbox environment and observing their behavior and network interactions. Dynamic analysis can uncover unknown malware that may evade static analysis or signature-based detection methods.
Start a Discussions
Click the Exhibit button.
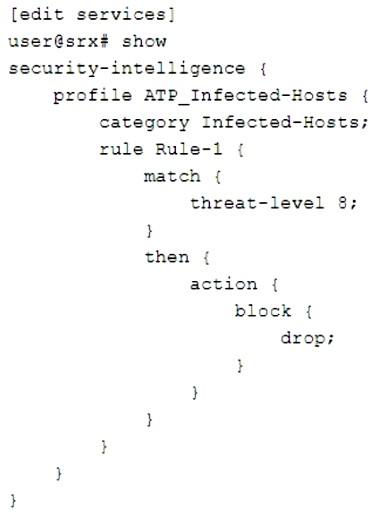
Referring to the exhibit, what will the SRX Series device do in this configuration?
Correct : C
The exhibit shows a configuration snippet for security intelligence on an SRX Series device. Security intelligence is a feature that allows you to block or monitor traffic from malicious sources based on threat intelligence feeds from Juniper ATP Cloud or other providers. The configuration defines a profile for ATP Infected-Hosts, which is a feed that contains IP addresses of hosts that are infected with malware and communicate with command-and-control servers. The configuration also defines a rule for threat level 8, which is a parameter that indicates the severity of the threat. Based on this configuration, the SRX Series device will do the following:
Packets from the infected hosts with a threat level of 8 or above will be dropped: The action block-and-drop under the rule means that the device will block any traffic from the infected hosts that have a threat level equal to or higher than 8. This will prevent the hosts from sending or receiving malicious commands or data.
No log message will be generated: The absence of any log option under the rule means that the device will not generate any log message for the blocked traffic. This may reduce the load on the device and the logging server, but it may also limit the visibility and analysis of the security events.
Start a Discussions
You want to control when cluster failovers occur.
In this scenario, which two specific parameters would you configure on an SRX Series device? (Choose two.)
Start a Discussions
You administer a JSA host and want to include a rule that sets a threshold for excessive firewall denies and sends an SNMP trap after receiving related syslog messages from an SRX Series firewall.
Which JSA rule type satisfies this requirement?
Start a Discussions
You are implementing an SRX Series device at a branch office that has low bandwidth and also uses a cloud-based VoIP solution with an outbound policy that permits all traffic.
Which service would you implement at your edge device to prioritize VoIP traffic in this scenario?
Correct : D
The service that you would implement at your edge device to prioritize VoIP traffic in this scenario is AppQoS. AppQoS is a feature that enables you to allocate bandwidth and prioritize traffic based on application signatures or custom rules. AppQoS can enhance the quality of service and experience for critical or latency-sensitive applications, such as VoIP. You can configure AppQoS policies to assign different classes of service (CoS) values or queue numbers to different applications or traffic flows. You can also define bandwidth limits, guarantees, or bursts for each class or queue.Reference:= [Application Quality of Service Overview], [Configuring Application Quality of Service]
Start a Discussions
Total 98 questions