Curious about Actual GAQM GAQM CEH (CPEH-001) Exam Questions?
Here are sample GAQM Certified Professional Ethical Hacker (CPEH) (CPEH-001) Exam questions from real exam. You can get more GAQM GAQM CEH (CPEH-001) Exam premium practice questions at TestInsights.
Neil is closely monitoring his firewall rules and logs on a regular basis. Some of the users have complained to Neil that there are a few employees who are visiting offensive web site during work hours, without any consideration for others. Neil knows that he has an up-to-date content filtering system and such access should not be authorized. What type of technique might be used by these offenders to access the Internet without restriction?
Correct : D
This can be accomplished by, for example, tunneling the http traffic over SSH if you have a SSH server answering to your connection, you enable dynamic forwarding in the ssh client and configure Internet Explorer to use a SOCKS Proxy for network traffic.
Start a Discussions
Eric notices repeated probes to port 1080. He learns that the protocol being used is designed to allow a host outside of a firewall to connect transparently and securely through the firewall. He wonders if his firewall has been breached. What would be your inference?
Correct : D
Port Description:
SOCKS. SOCKS port, used to support outbound tcp services (FTP, HTTP, etc). Vulnerable similar to FTP Bounce, in that attacker can connect to this port and \bounce\ out to another internal host. Done to either reach a protected internal host or mask true source of attack. Listen for connection attempts to this port -- good sign of port scans, SOCKS-probes, or bounce attacks. Also a means to access restricted resources. Example: Bouncing off a MILNET gateway SOCKS port allows attacker to access web sites, etc. that were restricted only to.mil domain hosts.
Start a Discussions
Exhibit:
Given the following extract from the snort log on a honeypot, what service is being exploited? :
Correct : A
The connection is done to 172.16.1.104:21.
Start a Discussions
There are two types of honeypots- high and low interaction. Which of these describes a low interaction honeypot? Select the best answers.
Correct : A, C, D, E
Start a Discussions
The following exploit code is extracted from what kind of attack?
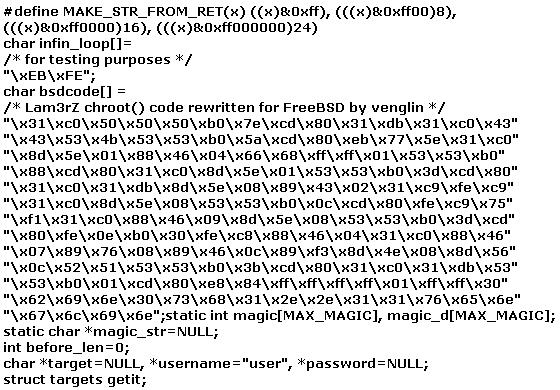
Correct : E
This is a buffer overflow with it's payload in hex format.
Start a Discussions
Total 877 questions