Curious about Actual Fortinet Certified Solution Specialist (NSE7_EFW-7.2) Exam Questions?
Here are sample Fortinet NSE 7 - Enterprise Firewall 7.2 (NSE7_EFW-7.2) Exam questions from real exam. You can get more Fortinet Certified Solution Specialist (NSE7_EFW-7.2) Exam premium practice questions at TestInsights.
You want to block access to the website ww.eicar.org using a custom IPS signature.
Which custom IPS signature should you configure?
A)

B)

C)

D)
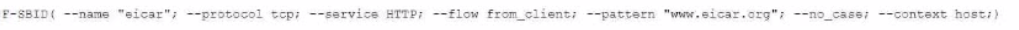
Start a Discussions
Exhibit.
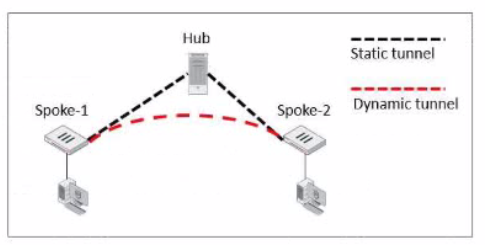
Refer to the exhibit, which shows an ADVPN network.
The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
Which first message floes the hub send to Spoke-110 bring up the dynamic tunnel?
Correct : A
In an ADVPN scenario, when traffic is initiated from a client behind one spoke to another spoke, the hub sends a shortcut query to the initiating spoke. This query is used to determine if there is a more direct path for the traffic, which can then trigger the establishment of a dynamic tunnel between the spokes.
Start a Discussions
Exhibit.
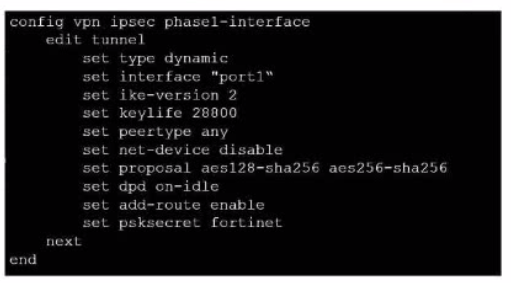
Refer to the exhibit, which contains a partial VPN configuration.
What can you conclude from this configuration1?
Correct : C
From the given VPN configuration, dead peer detection (DPD) is set to 'on-idle', indicating that DPD is enabled and will be used to detect if the other end of the VPN tunnel is still alive when no traffic is detected. Hence, option C is incorrect. The configuration shows the tunnel set to type 'dynamic', which does not create separate virtual interfaces for each dial-up client (A), and it is not specified that dynamic routing will be used (B). Since this is a phase 1 configuration snippet, the routing table aspect (D) cannot be concluded from this alone.
Start a Discussions
You contoured an address object on the tool fortiGate in a Security Fabric. This object is not synchronized with a downstream device. Which two reasons could be the cause? (Choose two)
Correct : A, C
1: Group address objects synchronized from FortiManager5
2: Security Fabric address object unification6
3: Configuration synchronization7
4: Configuration synchronization7
: Security Fabric - Fortinet Documentation
Start a Discussions
Which two statements about the BFD parameter in BGP are true? (Choose two.)
Correct : A, C
Bidirectional Forwarding Detection (BFD) is a rapid protocol for detecting failures in the forwarding path between two adjacent routers, including interfaces, data links, and forwarding planes. BFD is designed to detect forwarding path failures in a very short amount of time, often less than one second, which is significantly faster than traditional failure detection mechanisms like hold-down timers in routing protocols.
Fortinet supports BFD for BGP, and it can be used over multiple hops, which allows the detection of failures even if the BGP peers are not directly connected. This functionality enhances the ability to maintain stable BGP sessions over a wider network topology and is documented in Fortinet's guides.
Start a Discussions
Total 64 questions