Curious about Actual Fortinet Certified Solution Specialist (FCSS_EFW_AD-7.4) Exam Questions?
Here are sample Fortinet FCSS - Enterprise Firewall 7.4 Administrator (FCSS_EFW_AD-7.4) Exam questions from real exam. You can get more Fortinet Certified Solution Specialist (FCSS_EFW_AD-7.4) Exam premium practice questions at TestInsights.
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
Correct : A, B
The Internet Service Database (ISDB) in FortiGate is used to enforce content filtering at Layer 3 (Network Layer) and Layer 4 (Transport Layer) of the OSI model by identifying applications based on their predefined IP addresses and ports.
FortiGate has a predefined list of all IPs and ports for specific applications downloaded from FortiGuard:
FortiGate retrieves and updates a predefined list of IPs and ports for different internet services from FortiGuard.
This allows FortiGate to block specific services at Layer 3 and Layer 4 without requiring deep packet inspection.
The ISDB blocks the IP addresses and ports of an application predefined by FortiGuard:
ISDB works by matching traffic to known IP addresses and ports of categorized services.
When an application or service is blocked, FortiGate prevents communication by denying traffic based on its destination IP and port number.
Start a Discussions
Refer to the exhibits.
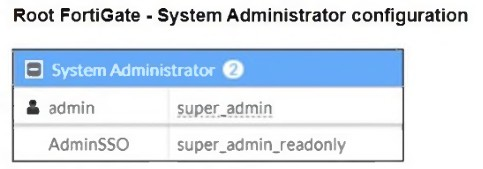
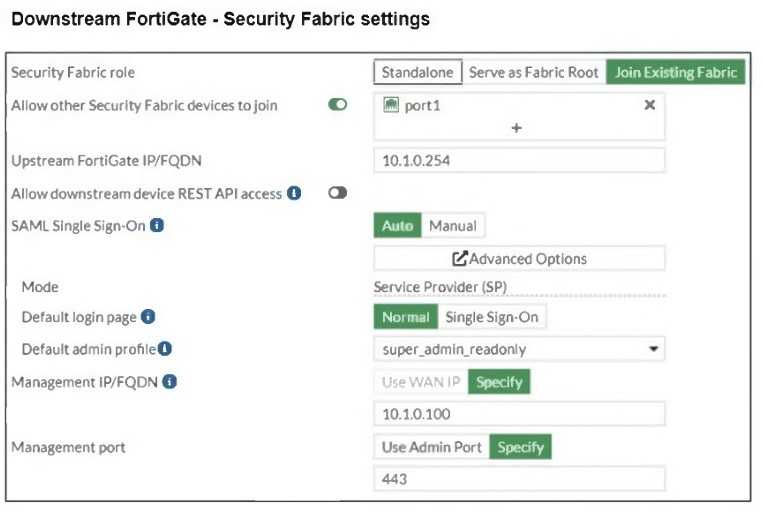
The Administrators section of a root FortiGate device and the Security Fabric Settings section of a downstream FortiGate device are shown.
When prompted to sign in with Security Fabric in the downstream FortiGate device, a user enters the AdminSSO credentials.
What is the next status for the user?
Correct : C
From the Root FortiGate - System Administrator Configuration exhibit:
The AdminSSO account has the super_admin_readonly role.
From the Downstream FortiGate - Security Fabric Settings exhibit:
The Security Fabric role is set to Join Existing Fabric, meaning it will authenticate with the root FortiGate.
SAML Single Sign-On (SSO) is enabled, and the default admin profile is set to super_admin_readonly.
When the AdminSSO user logs into the downstream FortiGate using SSO, the authentication request is sent to the root FortiGate, where AdminSSO has super_admin_readonly permissions. Since the downstream FortiGate inherits this permission through the Security Fabric configuration, the user will be granted super_admin_readonly access.
Start a Discussions
A user reports that their computer was infected with malware after accessing a secured HTTPS website. However, when the administrator checks the FortiGate logs, they do not see that the website was detected as insecure despite having an SSL certificate and correct profiles applied on the policy.
How can an administrator ensure that FortiGate can analyze encrypted HTTPS traffic on a website?
Correct : D
FortiGate, like other security appliances, cannot analyze encrypted HTTPS traffic unless it decrypts it first. If only certificate inspection is enabled, FortiGate can see the certificate details (such as the domain and issuer) but cannot inspect the actual web content.
To fully analyze the traffic and detect potential malware threats:
Full SSL inspection (Deep Packet Inspection) must be enabled in the SSL/SSH Inspection Profile.
This allows FortiGate to decrypt the HTTPS traffic, inspect the content, and then re-encrypt it before forwarding it to the user.
Without full SSL inspection, threats embedded in encrypted traffic may go undetected.
Start a Discussions
Refer to the exhibit, which shows an ADVPN network.
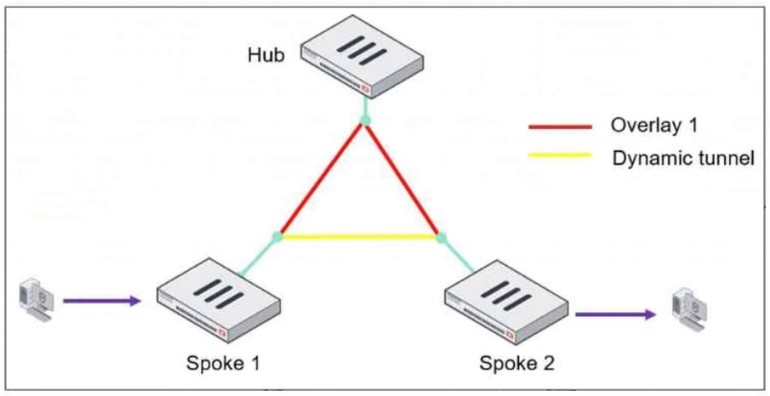
The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?
Correct : B
In an ADVPN (Auto-Discovery VPN) network, a dynamic VPN tunnel is established on-demand between spokes to optimize traffic flow and reduce latency.
Process:
1. Traffic Initiation:
2. Hub Detection:
3. Shortcut Offer:
4. Tunnel Establishment:
Start a Discussions
What is the initial step performed by FortiGate when handling the first packets of a session?
Correct : C
When FortiGate processes the first packets of a session, it follows a sequence of steps to determine how the traffic should be handled before establishing a session. The initial step involves:
Access Control List (ACL) checks: Determines if the traffic should be allowed or blocked based on predefined security rules.
Hardware Packet Engine (HPE) inspections: Ensures that packet headers are valid and comply with protocol standards.
IP Integrity Header Checking: Verifies if the IP headers are intact and not malformed or spoofed.
Once these security inspections are completed and the session is validated, FortiGate then installs the session in hardware (if offloading is enabled) or processes it in software.
Start a Discussions
Total 57 questions