Curious about Actual Fortinet Certified Professional (FCP_FCT_AD-7.2) Exam Questions?
Here are sample Fortinet FCP - FortiClient EMS 7.2 Administrator (FCP_FCT_AD-7.2) Exam questions from real exam. You can get more Fortinet Certified Professional (FCP_FCT_AD-7.2) Exam premium practice questions at TestInsights.
Refer to the exhibit.
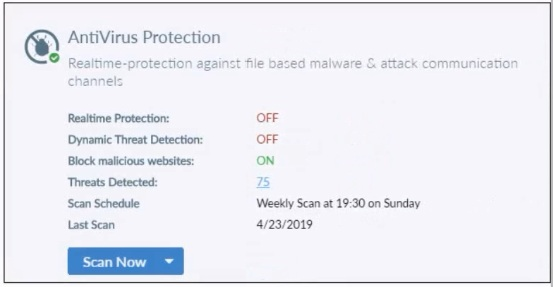
Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?
Correct : D
Block Malicious Website has nothing to do with infected files. Since Realtime Protection is OFF, it will be allowed without being scanned.
Based on the settings shown in the exhibit:
Realtime Protection: OFF
Dynamic Threat Detection: OFF
Block malicious websites: ON
Threats Detected: 75
The 'Realtime Protection' setting is crucial for preventing infected files from being downloaded and executed. Since 'Realtime Protection' is OFF, FortiClient will not actively scan files being downloaded. The setting 'Block malicious websites' is intended to prevent access to known malicious websites but does not scan files for infections.
Therefore, when a user tries to download an infected file, FortiClient will allow the file to download without scanning it due to the Realtime Protection being OFF.
Reference
FortiClient EMS 7.2 Study Guide, Antivirus Protection Section
Fortinet Documentation on FortiClient Real-time Protection Settings
Start a Discussions
An administrator deploys a FortiClient installation through the Microsoft AD group policy After installation is complete all the custom configuration is missing.
What could have caused this problem?
Correct : D
When deploying FortiClient via Microsoft AD Group Policy, it is essential to ensure that the deployment package is correctly assigned to the target group. The absence of custom configuration after installation can be due to several reasons, but the most likely cause is:
Deployment Package Assignment: The FortiClient package must be assigned to the appropriate group in Group Policy Management. If this step is missed, the installation may proceed, but the custom configurations will not be applied.
Thus, the administrator must ensure that the FortiClient package is correctly assigned to the group to include all custom configurations.
Reference
FortiClient EMS 7.2 Study Guide, Deployment and Installation Section
Fortinet Documentation on FortiClient Deployment using Microsoft AD Group Policy
Start a Discussions
Refer to the exhibits.
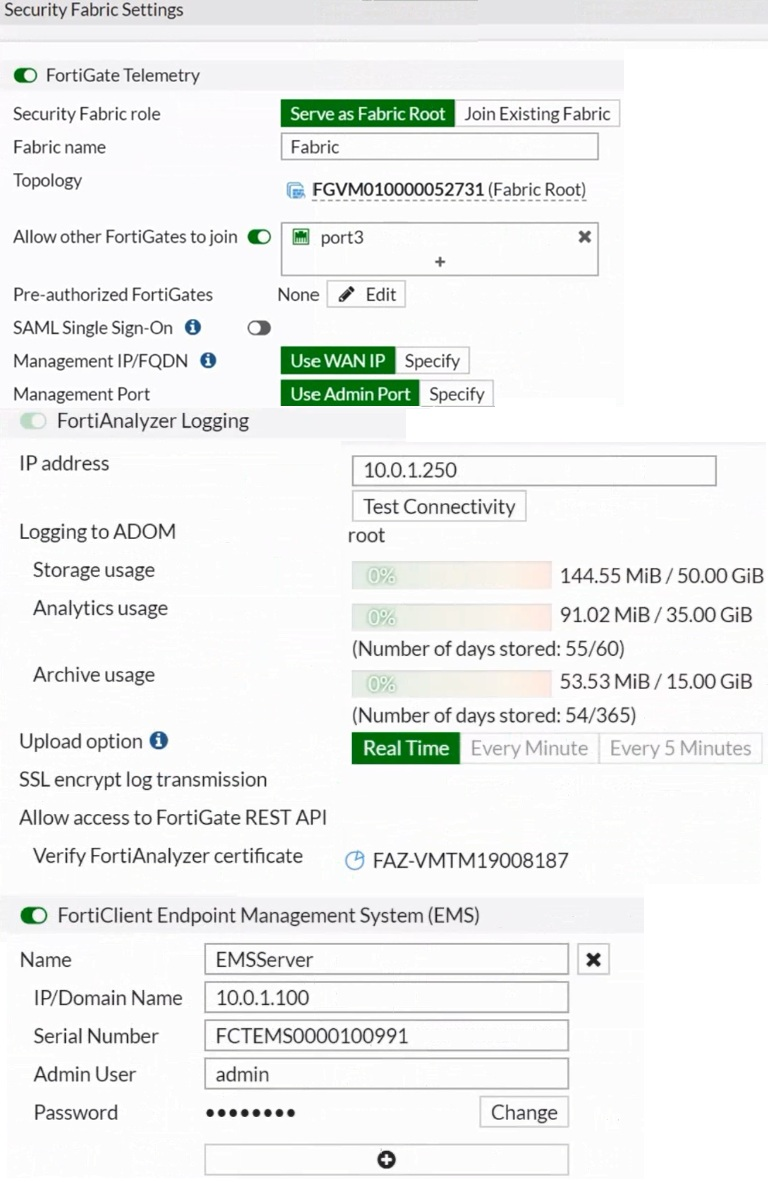
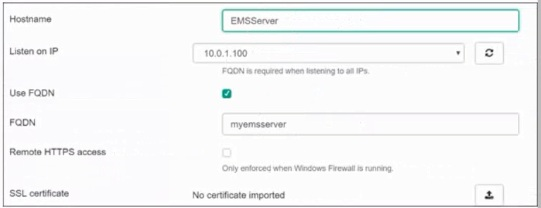
Based on the FortiGate Security Fabric settings shown in the exhibits, what must an administrator do on the EMS server to successfully quarantine an endpoint. when it is detected as a compromised host (loC)?
Correct : A
Based on the FortiGate Security Fabric settings shown in the exhibits, to successfully quarantine an endpoint when it is detected as a compromised host (IOC), the following step is required:
Enable Remote HTTPS Access to EMS: This setting allows FortiGate to communicate securely with FortiClient EMS over HTTPS. Remote HTTPS access is essential for the quarantine functionality to operate correctly, enabling the EMS server to receive and act upon the quarantine commands from FortiGate.
Therefore, the administrator must enable remote HTTPS access to EMS to allow the quarantine process to function properly.
Reference
FortiGate Infrastructure 7.2 Study Guide, Security Fabric and Integration with EMS Sections
Fortinet Documentation on Enabling Remote HTTPS Access to FortiClient EMS
Start a Discussions
Which statement about FortiClient comprehensive endpoint protection is true?
Correct : D
FortiClient provides comprehensive endpoint protection for your Windows-based, Mac-based, and Linuxbased desktops, laptops, file servers, and mobile devices such as iOS and Android. It helps you to safeguard your systems with advanced security technologies, all of which you can manage from a single management console.
Start a Discussions
Refer to the exhibit.
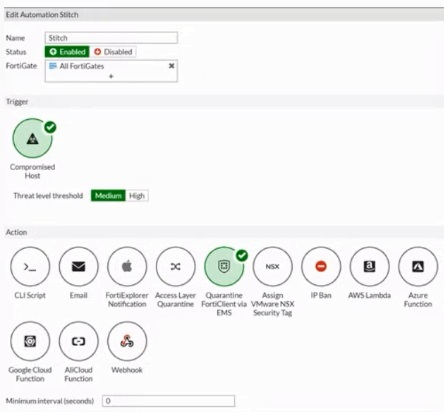
Based on the Security Fabric automation settings, what action will be taken on compromised endpoints?
Correct : A
Based on the Security Fabric automation settings shown in the exhibit:
The automation stitch is configured with a trigger for a 'Compromised Host.'
The action specified for this trigger is 'Quarantine FortiClient via EMS.'
This indicates that when an endpoint is detected as compromised, FortiClient EMS will quarantine the endpoint as part of the automation process.
Therefore, the action taken on compromised endpoints will be to quarantine them through EMS.
Reference
FortiGate Security 7.2 Study Guide, Automation Stitches and Actions Section
Fortinet Documentation on Configuring Automation Stitches and Quarantine Actions
Start a Discussions
Total 55 questions