Curious about Actual Eccouncil Certified Application Security Engineer (312-96) Exam Questions?
Here are sample Eccouncil Certified Application Security Engineer (CASE) JAVA (312-96) Exam questions from real exam. You can get more Eccouncil Certified Application Security Engineer (312-96) Exam premium practice questions at TestInsights.
Oliver is a web server admin and wants to configure the Tomcat server in such a way that it should not serve index pages in the absence of welcome files. Which of the following settings in CATALINA_HOME/conf/ in web.xml will solve his problem?
Correct : B
Start a Discussions
James is a Java developer working INFR INC. He has written Java code to open a file, read it line by line and display its content in the text editor. He wants to ensure that any unhandled exception raised by the code should automatically close the opened file stream. Which of the following exception handling block should he use for the above purpose?
Correct : C
Start a Discussions
Which of the following can be derived from abuse cases to elicit security requirements for software system?
Correct : D
Start a Discussions
Which of the following state management method works only for a sequence of dynamically generated forms?
Correct : C
Start a Discussions
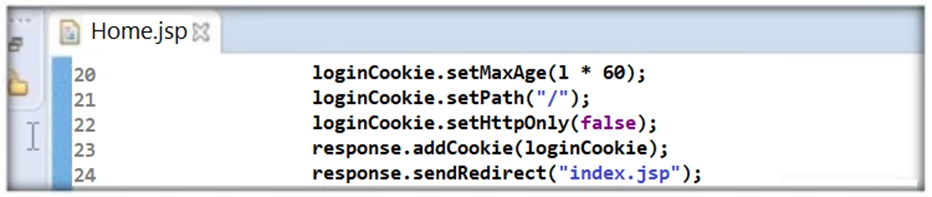
Thomas is not skilled in secure coding. He neither underwent secure coding training nor is aware of the consequences of insecure coding. One day, he wrote code as shown in the following screenshot. He passed 'false' parameter to setHttpOnly() method that may result in the existence of a certain type of vulnerability. Identify the attack that could exploit the vulnerability in the above case.
Correct : B
Start a Discussions
Total 47 questions