Curious about Actual CompTIA Cloud+ (CV0-004) Exam Questions?
Here are sample CompTIA Cloud+ (2025) (CV0-004) Exam questions from real exam. You can get more CompTIA Cloud+ (CV0-004) Exam premium practice questions at TestInsights.
A cloud engineer is deploying a cloud solution that will be used on premises with need-to-know access. Which of the following cloud deployment models best meets this
requirement?
Correct : C
A private cloud deployment model is the most appropriate when the requirement is for 'need-to-know' access, as it offers a more secure environment with resources dedicated to a single organization. It can be hosted on-premises or off-premises but is maintained on a private network, ensuring greater control over the data, security, and compliance when compared to other cloud models. Reference: CompTIA Cloud+ Certification Study Guide (Exam CV0-004) by Scott Wilson and Eric Vanderburg
Start a Discussions
A cloud engineer is designing a high-performance computing cluster for proprietary software. The software requires low network latency and high throughput between cluster nodes.
Which of the following would have the greatest impact on latency and throughput when designing the HPC infrastructure?
Correct : A
Node placement is critical in high-performance computing (HPC) clusters where low network latency and high throughput are required. Proper placement of nodes within the network infrastructure, including proximity to each other and to key network components, can significantly reduce latency and increase throughput. Ensuring that nodes are physically close and well-connected can facilitate faster data transfer rates between them. Reference: CompTIA Cloud+ Certification Study Guide (Exam CV0-004) by Scott Wilson and Eric Vanderburg
Start a Discussions
A security team recently hired multiple interns who all need the same level of access. Which of the following controls should the security team implement to provide access to the
cloud environment with the least amount of overhead?
Correct : D
Implementing group-based access control is the most efficient way to provide access to multiple interns who require the same level of access. This method allows the security team to assign permissions to a group rather than to individual user accounts, thereby reducing the administrative overhead involved in managing access rights for each intern individually. Reference: CompTIA Cloud+ Certification Study Guide (Exam CV0-004) by Scott Wilson and Eric Vanderburg
Start a Discussions
A cloud security analyst is investigating the impact of a recent cyberattack. The analyst is reviewing the following information:
Web server access log:
104.210.233.225 - - [21/10/2022:11:17: 40] "POST /uploadfile.html?f=myfile.php" 200 1638674
45.32.10.66 - - [21/10/2022:11:19:12] "GET /welcome.html" 200 5812
104.210.233.225 - - [21/10/2022:11:21:19] "GET / .. / .. / .. / .. /conf/server.xml HTTP/1.1" 200 74458
45.32.10.66 - - [21/10/22:11:22:32] "GET /admin.html HTTP/1.1" 200 9518
Web application firewall log:
"2022/10/21 11:17:33" "10.25.2.35" "104. 210.233.225" "userl" "File transfer completed successfully."
"2022/10/21 11:21:05" "10. 25.2. 35" "104. 210.233.225" "userl" "Accessed application page."
"2022/10/21 11:22:13" "10.25.2.35" "45. 32. 10. 66" "user2" "Accessing admin page. "
Which of the following has occurred?
Correct : D
The logs indicate that the IP address 104.210.233.225 made a GET request that appears to traverse directories (as indicated by the '/../../') to access 'server.xml', which is a configuration file for the server. This type of request is indicative of a directory traversal attack, which can lead to unauthorized access to sensitive files on the server. The successful 200 response code suggests that the file was accessed, implying that sensitive configuration data could have been leaked. Reference: CompTIA Cloud+ Certification Study Guide (Exam CV0-004) by Scott Wilson and Eric Vanderburg
Start a Discussions
A systems administrator notices a surge of network traffic is coming from the monitoring server. The administrator discovers that large amounts of data are being downloaded to an external source. While investigating, the administrator reviews the following logs:
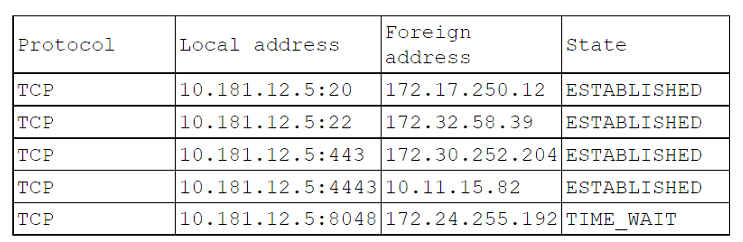
Which of the following ports has been compromised?
Correct : E
Based on the logs provided, the port that has been compromised is Port 8048. The state 'TIME_WAIT' indicates that this port was recently used to establish a connection that has now ended. This could be indicative of the recent activity where large amounts of data were downloaded to an external source, suggesting a potential security breach. Reference: CompTIA Cloud+ Study Guide (Exam CV0-004) by Todd Montgomery and Stephen Olson
Start a Discussions
Total 229 questions