Curious about Actual CompTIA SecurityX (CAS-005) Exam Questions?
Here are sample CompTIA SecurityX Certification (CAS-005) Exam questions from real exam. You can get more CompTIA SecurityX (CAS-005) Exam premium practice questions at TestInsights.
A company plans to implement a research facility with Intellectual property data that should be protected The following is the security diagram proposed by the security architect
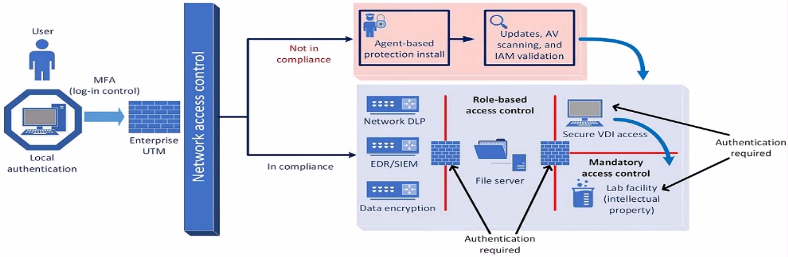
Which of the following security architect models is illustrated by the diagram?
Correct : D
The security diagram proposed by the security architect depicts a Zero Trust security model. Zero Trust is a security framework that assumes all entities, both inside and outside the network, cannot be trusted and must be verified before gaining access to resources.
Key Characteristics of Zero Trust in the Diagram:
Role-based Access Control: Ensures that users have access only to the resources necessary for their role.
Mandatory Access Control: Additional layer of security requiring authentication for access to sensitive areas.
Network Access Control: Ensures that devices meet security standards before accessing the network.
Multi-factor Authentication (MFA): Enhances security by requiring multiple forms of verification.
This model aligns with the Zero Trust principles of never trusting and always verifying access requests, regardless of their origin.
CompTIA SecurityX Study Guide
NIST Special Publication 800-207, 'Zero Trust Architecture'
'Implementing a Zero Trust Architecture,' Forrester Research
Start a Discussions
A financial services organization is using Al lo fully automate the process of deciding client loan rates Which of the following should the organization be most concerned about from a privacy perspective?
Correct : A
When using AI to fully automate the process of deciding client loan rates, the primary concern from a privacy perspective is model explainability.
Why Model Explainability is Critical:
Transparency: It ensures that the decision-making process of the AI model can be understood and explained to stakeholders, including clients.
Accountability: Helps in identifying biases and errors in the model, ensuring that the AI is making fair and unbiased decisions.
Regulatory Compliance: Various regulations require that decisions, especially those affecting individuals' financial status, can be explained and justified.
Trust: Builds trust among users and stakeholders by demonstrating that the AI decisions are transparent and justifiable.
Other options, such as credential theft, prompt injections, and social engineering, are significant concerns but do not directly address the privacy and fairness implications of automated decision-making.
CompTIA SecurityX Study Guide
'The Importance of Explainability in AI,' IEEE Xplore
GDPR Article 22, 'Automated Individual Decision-Making, Including Profiling'
Start a Discussions
A company wants to use loT devices to manage and monitor thermostats at all facilities The thermostats must receive vendor security updates and limit access to other devices within the organization Which of the following best addresses the company's requirements''
Correct : B
The best approach for managing and monitoring IoT devices, such as thermostats, is to operate them on a separate network with no access to other internal devices. This segmentation ensures that the IoT devices are isolated from the main network, reducing the risk of potential security breaches affecting other critical systems. Additionally, this setup allows for secure vendor updates without exposing the broader network to potential vulnerabilities inherent in IoT devices.
CompTIA SecurityX Study Guide: Recommends network segmentation for IoT devices to minimize security risks.
NIST Special Publication 800-183, 'Network of Things': Advises on the isolation of IoT devices to enhance security.
'Practical IoT Security' by Brian Russell and Drew Van Duren: Discusses best practices for securing IoT devices, including network segmentation.
Start a Discussions
An engineering team determines the cost to mitigate certain risks is higher than the asset values The team must ensure the risks are prioritized appropriately. Which of the following is the best way to address the issue?
Correct : D
When the cost to mitigate certain risks is higher than the asset values, the best approach is to purchase insurance. This method allows the company to transfer the risk to an insurance provider, ensuring that financial losses are covered in the event of an incident. This approach is cost-effective and ensures that risks are prioritized appropriately without overspending on mitigation efforts.
CompTIA SecurityX Study Guide: Discusses risk management strategies, including risk transfer through insurance.
NIST Risk Management Framework (RMF): Highlights the use of insurance as a risk mitigation strategy.
'Information Security Risk Assessment Toolkit' by Mark Talabis and Jason Martin: Covers risk management practices, including the benefits of purchasing insurance.
Start a Discussions
Company A acquired Company B and needs to determine how the acquisition will impact the attack surface of the organization as a whole. Which of the following is the best way to achieve this goal? (Select two).
Implementing DLP controls preventing sensitive data from leaving Company B's network
Correct : A, B
To determine how the acquisition of Company B will impact the attack surface, the following steps are crucial:
A . Documenting third-party connections used by Company B: Understanding all external connections is essential for assessing potential entry points for attackers and ensuring that these connections are secure.
E . Performing an architectural review of Company B's network: This review will identify vulnerabilities and assess the security posture of the acquired company's network, providing a comprehensive understanding of the new attack surface.
These actions will provide a clear picture of the security implications of the acquisition and help in developing a plan to mitigate any identified risks.
CompTIA SecurityX Study Guide: Emphasizes the importance of understanding third-party connections and conducting architectural reviews during acquisitions.
NIST Special Publication 800-37, 'Guide for Applying the Risk Management Framework to Federal Information Systems': Recommends comprehensive reviews and documentation of third-party connections.
'Mergers, Acquisitions, and Other Restructuring Activities' by Donald DePamphilis: Discusses the importance of security assessments during acquisitions.
Start a Discussions
Total 217 questions