Curious about Actual CompTIA CASP (CAS-004) Exam Questions?
Here are sample CompTIA Advanced Security Practitioner (CASP+) (CAS-004) Exam questions from real exam. You can get more CompTIA CASP (CAS-004) Exam premium practice questions at TestInsights.
A security engineer is assessing a legacy server and needs to determine if FTP is running and on which port The service cannot be turned off, as it would impact a critical application's ability to function. Which of the following commands would provide the information necessary to create a firewall rule to prevent that service from being exploited?
Correct : C
The netstat -tulpn command is used to display network connections, routing tables, interface statistics, masquerade connections, and multicast memberships. The -tulpn options specifically show TCP and UDP connections with the process ID and the name that is listening on each port, which would provide the necessary information to identify if FTP is running and on which port without turning the service off. This information can then be used to create a precise firewall rule to prevent the FTP service from being exploited.
Start a Discussions
A SOC analyst received an alert about a potential compromise and is reviewing the following SIEM logs:
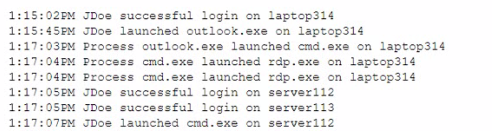
Which of the following is the most appropriate action for the SOC analyst to recommend?
Correct : B
The SIEM logs indicate suspicious behavior that could be a sign of a compromise, such as the launching of cmd.exe after Outlook.exe, which is atypical user behavior and could indicate that a machine has been compromised to perform lateral movement within the network. Isolating laptop314 from the network would contain the threat and prevent any potential spread to other systems while further investigation takes place.
Start a Discussions
A security administrator needs to recommend an encryption protocol after a legacy stream cipher was deprecated when a security flaw was discovered. The legacy cipher excelled at maintaining strong cryptographic security and provided great performance for a streaming video service. Which of the following AES modes should the security administrator recommend given these requirements?
Correct : D
Galois/Counter Mode (GCM) is an AES mode of operation that provides both confidentiality and data integrity. It is well-suited for processing streams of data, making it ideal for streaming video services. GCM is known for its strong cryptographic security and good performance, which aligns with the legacy cipher's characteristics and the streaming service's requirements.
Start a Discussions
Company A is merging with Company B Company A is a small, local company Company B has a large, global presence The two companies have a lot of duplication in their IT systems processes, and procedures On the new Chief Information Officer's (ClO's) first day a fire breaks out at Company B's mam data center Which of the following actions should the CIO take first?
Correct : B
In the event of a fire at the main data center, the immediate action should be to review and engage the disaster recovery plan. This is to ensure the continuity of business operations. The CIO should coordinate with IT leaders from both companies to ensure a unified response. Assessing the damage and planning for recovery are crucial, and leveraging the expertise from both companies can help streamline the process.
Start a Discussions
Law enforcement officials informed an organization that an investigation has begun. Which of the following is the FIRST step the organization should take?
Correct : A
A legal hold is a process by which an organization instructs its employees or other relevant parties to preserve specific data for potential litigation. A legal hold is triggered when litigation is reasonably anticipated, such as when law enforcement officials inform an organization that an investigation has begun. The first step the organization should take is to initiate a legal hold to ensure that relevant evidence is not deleted, destroyed, or altered. A legal hold also demonstrates the organization's good faith and compliance with its duty to preserve evidence. Verified Reference:
https://percipient.co/litigation-hold-triggers-and-the-duty-to-preserve-evidence/
Start a Discussions
Total 611 questions