Curious about Actual Cisco CCIE (350-501) Exam Questions?
Here are sample Cisco Implementing and Operating Cisco Service Provider Network Core Technologies (350-501) Exam questions from real exam. You can get more Cisco CCIE (350-501) Exam premium practice questions at TestInsights.
A mod-size service provider uses L2VPN as its standard for connectivity between offices. A small company wants the service provider to connect the company's two sites across the service provider core. To meet service requirements, the service provider must extend the layer 2 domain between the company's two locations. Which configuration must the engineer apply to implement an attachment circuit between the two sites using a VLAN tag of 12?
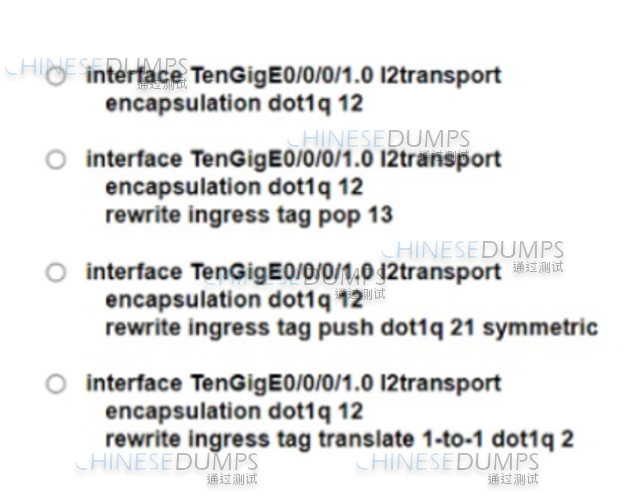
Correct : C
The correct configuration for extending the layer 2 domain between the company's two locations involves setting up the interface with L2 transport, specifying the encapsulation method as dot1q with the VLAN tag of 12, and applying the appropriate rewrite ingress tag rules. This setup ensures that the VLAN tag is preserved across the service provider's core, maintaining the layer 2 domain continuity.
Start a Discussions
According to RFC5305 on IS-IS extensions for traffic engineering, what is the 4-octet sub-TLV type 10 of extended IS-IS reachability TLV type 22?
Start a Discussions
Refer to the exihibit.
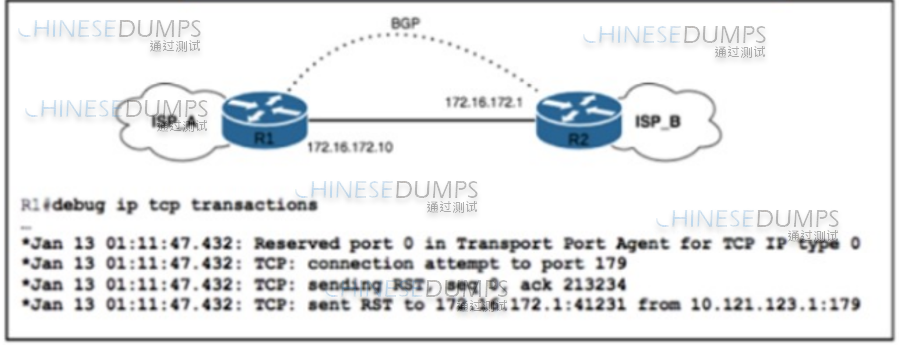
Refer to the exhibit. ISP_A and ISP_B use AS numbers 38321 and 16213 respectively. After a network engineer reloaded router R1, the BGP session with R2 failed to establish. The engineer confirmed BGP next-hop availability with a connectivity test between the router loopback addresses 10.121.123.2 and 10.121.123.1, as well as between interfaces Gi1/1 and Gi1/2. EBGP multihop has been configured on both routers. Which action must the engineer take to resolve the issue?
Start a Discussions
Refer to the exihibit.
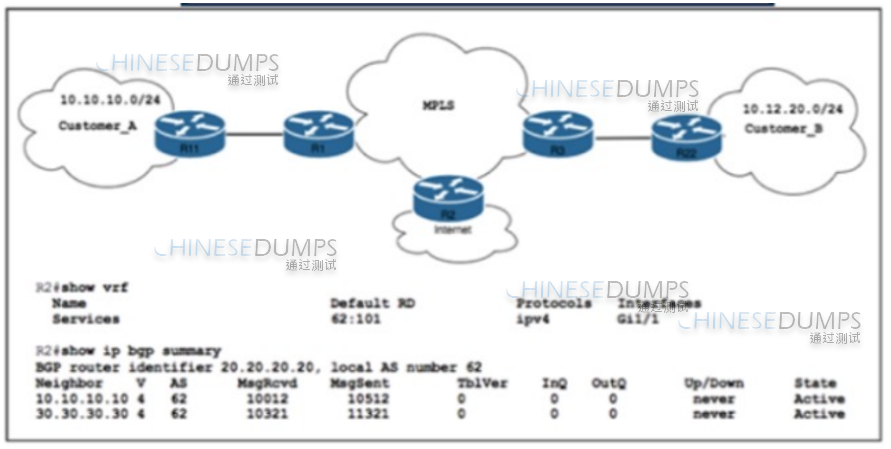
Refer to the exhibit. ISP_A is about to launch a new internet service. ISP_A is already providing MPLS VPN Layer 3 services to Customer_A and Customer_B, which are connected to ISP_A via OSPF. A network engineer completed the BGP and VRF configurations on R2 to support the new internet service. Which additional action completed the launch?
Start a Discussions
Simulation 7
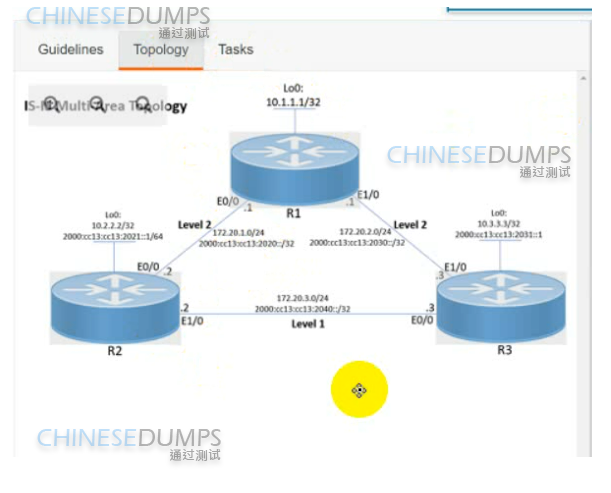
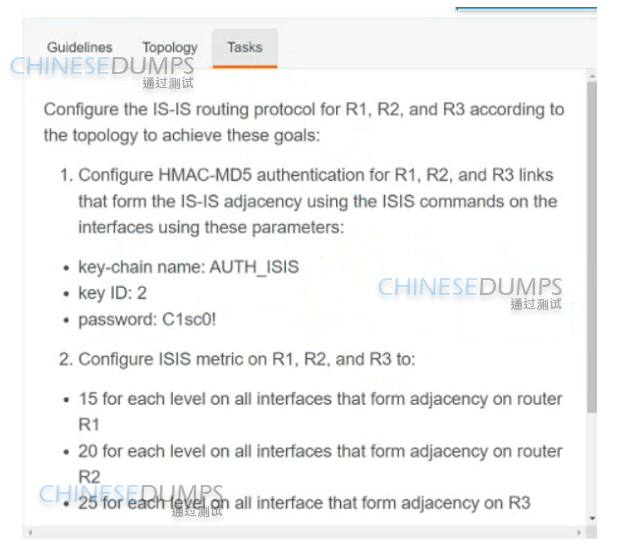
Correct : A
R1
key chain AUTH_ISIS
key 2
key-string C1sco!
exit
int range et0/0 , et1/0
isis authen key-chain AUTH_ISIS
ip isis
isis metric 15
Copy run start
R2
key chain AUTH_ISIS
key 2
key-string C1sco!
exit
int range et0/0 , et1/0
isis authen key-chain AUTH_ISIS
ip isis
isis metric 20
Copy run start
R3
key chain AUTH_ISIS
key 2
key-string C1sco!
exit
int range et0/0 , et1/0
isis authen key-chain AUTH_ISIS
ip isis
isis metric 25
Copy run start
Start a Discussions
Total 452 questions