Curious about Actual Cisco CCNP (300-710) Exam Questions?
Here are sample Cisco Securing Networks with Cisco Firepower (300-710) Exam questions from real exam. You can get more Cisco CCNP (300-710) Exam premium practice questions at TestInsights.
Refer to the exhibit.
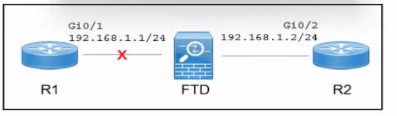
A Cisco Secure Firewall Threat Defense (FTD) device is deployed in inline mode with an inline set. The network engineer wants router R2 to remove the directly connected route M 68.1.0/24 from its routing table when the cable between routed R1 and the Secure FTD device Is disconnected. Which action must the engineer take?
1
Correct : A
To ensure that router R2 removes the directly connected route for 192.168.1.0/24 from its routing table when the cable between router R1 and the Secure FTD device is disconnected, the network engineer must implement the 'Propagate Link State' option on the Secure FTD device. This option allows the FTD to propagate the link state changes to adjacent devices, ensuring that the disconnection is recognized and the routing table is updated accordingly.
Steps:
Access the FTD device configuration via FMC.
Navigate to the interface settings for the relevant interfaces.
Enable the 'Propagate Link State' option for the interfaces connected to R1 and R2.
Deploy the changes to the FTD device.
This configuration ensures that the link state changes are communicated to router R2, prompting it to remove the disconnected route from its routing table.
Start a Discussions
Which component is needed to perform rapid threat containment with Cisco FMC?
Correct : A
To perform rapid threat containment with Cisco FMC, the necessary component is Cisco Identity Services Engine (ISE). ISE integrates with FMC to provide dynamic network access control and enforcement, allowing for quick isolation of compromised endpoints based on security events detected by FMC.
Steps:
Integrate FMC with ISE by configuring the necessary settings in both platforms.
Define security policies in FMC that trigger rapid threat containment actions via ISE.
When a threat is detected, FMC can instruct ISE to isolate the affected endpoint, limiting its access to the network.
This integration enables automated and efficient threat containment, reducing the response time and mitigating the impact of security incidents.
Start a Discussions
A security engineer must create a malware and file policy on a Cisco Secure Firewall Threat Defense device. The solution must ensure that PDF. DOCX, and XLSX files are not sent lo Cisco Secure Malware analytics. What must do configured to meet the requirements''
Correct : D
To create a malware and file policy on a Cisco Secure Firewall Threat Defense (FTD) device that ensures PDF, DOCX, and XLSX files are not sent to Cisco Secure Malware Analytics, the security engineer must configure local malware analysis. Local malware analysis allows the FTD to inspect and analyze files locally without sending them to the cloud-based Cisco Secure Malware Analytics.
Steps to configure local malware analysis:
In FMC, navigate to Policies > Access Control > Malware & File Policies.
Create a new malware and file policy or edit an existing one.
Define rules to inspect specific file types, ensuring that PDF, DOCX, and XLSX files are handled locally.
Set the action for these file types to 'Local Analysis.'
Apply the policy to the relevant access control policy.
This configuration ensures that the specified file types are analyzed locally, meeting the requirement to avoid sending them to Cisco Secure Malware Analytics.
Start a Discussions
An engineer must integrate a thud-party security Intelligence teed with Cisco Secure Firewall Management Center. Secure Firewall Management Center is running Version 6.2 3 and has 8 GB of memory. Which two actions must be taken to implement Throat Intelligence Director? (Choose two.)
Correct : A, C
To integrate a third-party security intelligence feed with Cisco Secure Firewall Management Center (FMC) using Threat Intelligence Director (TID), the following actions are necessary:
Upgrade to version 6.6: The FMC must be running at least version 6.6 to support Threat Intelligence Director. Version 6.2.3 does not support the necessary features for this integration.
Add the URL of the TAXII server: Threat Intelligence Director uses TAXII (Trusted Automated eXchange of Indicator Information) to pull threat intelligence data from third-party sources. The URL of the TAXII server must be added to the TID configuration in FMC.
Steps:
Upgrade FMC to version 6.6 or later.
In FMC, navigate to Integration > Threat Intelligence Director.
Add a new TAXII server by entering the URL of the TAXII server.
These actions enable the integration of third-party threat intelligence feeds, enhancing the security capabilities of the FMC.
Start a Discussions
An administrator configures the interfaces of a Cisco Secure Firewall Threat Defence device in an inline IPS deployment. The administrator completes these actions:
* identifies the device and the interfaces
* sets the interface mode to inline
* enables the interlaces
Which configuration step must the administrator take next to complete the implementation?
Correct : B
After setting the interface mode to inline and enabling the interfaces on a Cisco Secure Firewall Threat Defense (FTD) device in an inline IPS deployment, the next step is to configure an inline set. An inline set groups two interfaces that work together to inspect traffic passing between them.
Steps to configure an inline set:
In FMC, navigate to Devices > Device Management.
Select the FTD device and configure the interfaces.
Create a new inline set, adding the relevant interfaces that have been set to inline mode.
Deploy the configuration to the FTD device.
Configuring an inline set ensures that the traffic between the specified interfaces is inspected and processed according to the IPS policies, completing the implementation of the inline IPS deployment.
Start a Discussions
Total 325 questions