Curious about Actual Cisco Certified DevNet Associate (200-901) Exam Questions?
Here are sample Cisco DevNet Associate (200-901) Exam questions from real exam. You can get more Cisco Certified DevNet Associate (200-901) Exam premium practice questions at TestInsights.
Refer to the exhibit.
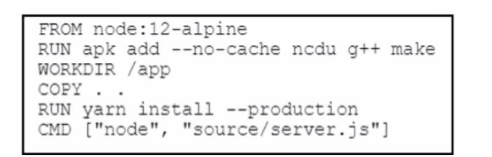
The server.js Node.js script runs after the Dockerfile creates its container. What is the working directory of the application inside the container?
Correct : B
In the given Dockerfile, the WORKDIR /app command sets the working directory for any subsequent commands to /app. This means that any commands following this line will be executed within the /app directory inside the Docker container. The COPY . . command copies the contents of the current directory on the host machine to the /app directory in the container. Finally, the CMD ['node', 'source/server.js'] command specifies the command to run when the container starts, which in this case is node source/server.js.
Dockerfile Reference - WORKDIR
Start a Discussions
Refer to the exhibit.
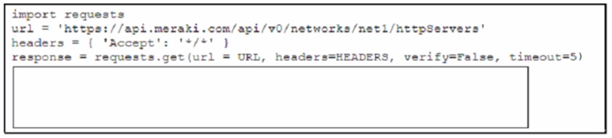
A developer creates a Python script by using the Cisco Meraki API. The solution must:
* Obtain a list of HTTP servers for a network named "netl".
* Print the response body if the HTTP status code is 200.
* Handle the timeout requests as exceptions, and print Timeout Error next to the exception to stdout.
Which block of code completes the script?
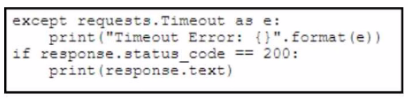
A)
B)
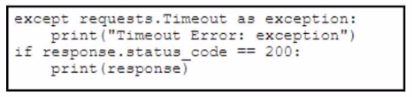
Correct : A
The block of code that correctly completes the script should handle timeout exceptions and print the error, as well as print the response body if the HTTP status code is 200. Option A achieves this:
import requests
url = 'https://api.meraki.com/api/v0/networks/net1/httpServers'
headers = { 'Accept': 'application/json' }
response = requests.get(url=url, headers=headers, verify=False, timeout=5)
try:
response = requests.get(url, headers=headers, verify=False, timeout=5)
response.raise_for_status()
except requests.Timeout as e:
print('Timeout Error: {}'.format(e))
if response.status_code == 200:
print(response.text)
This code makes a GET request to the specified URL, handles the timeout exception by printing a message, and prints the response body if the status code is 200.
Python Requests: Response Status Code
Start a Discussions
What is an advantage of device-level management as compared to controller-level management to automate the configuration of network devices?
Correct : B
Device-level management allows for more granular control over the specific settings and configurations of individual network devices. This is beneficial in scenarios where fine-tuning of device settings is required, and where certain configurations may not be exposed or supported by the overarching controller. Controller-level management, on the other hand, abstracts many device-specific settings to provide a more uniform and simplified management interface, which may not support all the detailed configurations available at the device level.
Cisco DevNet: Device vs. Controller Management
Start a Discussions
What is a benefit of organizing code into modules?
Correct : A
Organizing code into modules improves maintainability by encapsulating functionality into smaller, more manageable pieces. This modular approach allows developers to focus on specific sections of code without being overwhelmed by the entire codebase. It also makes it easier to debug, test, and update parts of the application independently, enhancing overall code quality and maintainability.
Start a Discussions
A resource named /item is protected by oAuth2 authentication. An endpoint named /login must request authentication. Which method must be used to access the resource by using the REST API?
Correct : B
When using OAuth2 authentication for accessing a protected resource via a REST API, the typical flow involves obtaining an access token which can then be used to authenticate subsequent API requests. The correct process is:
POST Call to /login: Make a POST request to the /login endpoint with the user credentials (username and password) in the request body. This call will authenticate the user and, if successful, return an access token.
Use the Token: Use the retrieved token by including it in the Authorization header (usually as a Bearer token) in the request to access the protected resource, in this case, the /item endpoint.
OAuth 2.0 Authorization Framework - RFC 6749
Start a Discussions
Total 481 questions