Curious about Actual Cisco Certified CyberOps Associate (200-201) Exam Questions?
Here are sample Cisco Understanding Cisco Cybersecurity Operations Fundamentals (200-201) Exam questions from real exam. You can get more Cisco Certified CyberOps Associate (200-201) Exam premium practice questions at TestInsights.
An engineer must investigate suspicious connections. Data has been gathered using a tcpdump command on a Linux device and saved as sandboxmatware2022-12-22.pcaps file. The engineer is trying to open the tcpdump in the Wireshark tool. What is the expected result?
Correct : B
Wireshark is a widely used network protocol analyzer that supports various capture file formats, including those generated by tcpdump.
The .pcap extension is a standard format for packet capture files and is fully supported by Wireshark.
The file extension or the inclusion of characters such as '-' in the file name does not impact Wireshark's ability to open and read the file.
When the engineer opens the sandboxmatware2022-12-22.pcaps file in Wireshark, the tool will read the packet capture data, allowing for detailed analysis of network traffic.
Cisco Cybersecurity Operations Fundamentals
Wireshark User Guide
tcpdump and libpcap Documentation
Start a Discussions
Refer to the exhibit.
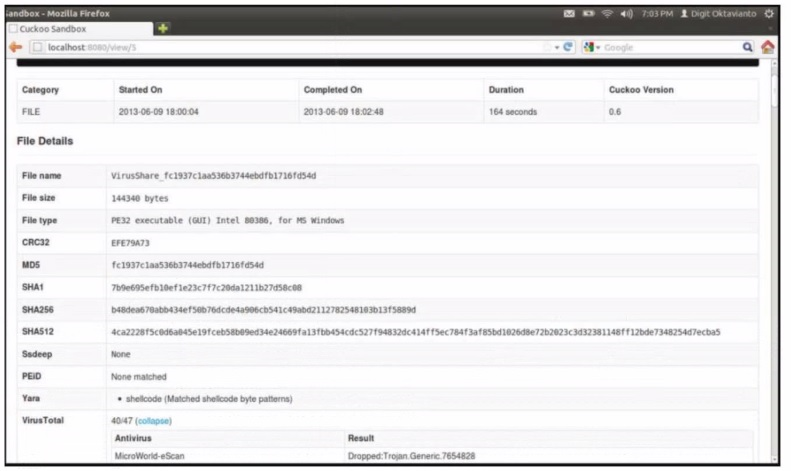
What does this Cuckoo sandbox report indicate?
Correct : C
The Cuckoo sandbox report shows the analysis results of a file named 'VirusShare_fc1937c1aa536b3744ebfb1716fd5f4d'.
The file type is identified as a PE32 executable for MS Windows.
The 'Yara' section indicates that the file contains shellcode, which matches specific shellcode byte patterns.
Shellcode typically indicates that the file will execute a payload, often used to open a command interpreter or execute commands directly.
Additionally, the antivirus result shows that the file was identified as containing a trojan (Trojan.Generic.7654828), which is consistent with behaviors such as opening a command interpreter for malicious purposes.
Cuckoo Sandbox Documentation
Analysis of Shellcode Behavior
Understanding Trojan Malware Functionality
Start a Discussions
A security engineer must protect the company from known issues that trigger adware. Recently new incident has been raised that could harm the system. Which security concepts are present in this scenario?
Correct : D
The security scenario involves protecting the company from known issues that trigger adware and addressing a recent incident that could harm the system.
This scenario involves identifying vulnerabilities (weaknesses in the system that can be exploited) and threats (potential harm that can exploit these vulnerabilities).
A vulnerability is an inherent flaw in the system, while a threat is an event or condition that has the potential to exploit the vulnerability.
The security engineer needs to assess both the vulnerabilities present and the threats that could exploit these vulnerabilities to implement effective protection measures.
Cisco Cybersecurity Operations Fundamentals
Concepts of Vulnerability and Threat in Cybersecurity
Best Practices in Vulnerability Management
Start a Discussions
An engineer configured regular expression ''.''\.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01]" on Cisco ASA firewall. What does this regular expression do?
Correct : D
The regular expression provided is: .\.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01]
This regular expression is designed to match file extensions for Word (.doc), Excel (.xls), and PowerPoint (.ppt) files in HTTP network sessions.
The regular expression uses character classes and alternatives to match different case variations of these file extensions.
The part .\.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) matches the file extensions, and HTTP/1 .[01] ensures that the match is in the context of HTTP version 1.0 or 1.1.
Cisco ASA Regular Expressions Documentation
Understanding Regular Expressions in Network Security
Filtering and Capturing HTTP Traffic with Regex
Start a Discussions
A user reports difficulties accessing certain external web pages. When an engineer examines traffic to and from the external domain in full packet captures, they notice that many SYNs have the same sequence number, source, and destination IP address, but they have different payloads. What is causing this situation?
Correct : A
TCP injection is an attack where the attacker sends crafted packets into an existing TCP session. These packets appear to be part of the session.
The presence of many SYN packets with the same sequence number, source, and destination IP but different payloads indicates that an attacker might be injecting packets into the session.
This method can be used to disrupt communication, inject malicious commands, or manipulate the data being transmitted.
Understanding TCP Injection Attacks
Analyzing Packet Captures for Injection Attacks
Network Security Monitoring Techniques
Start a Discussions
Total 375 questions